Testing the Azure AD (Entra ID) Join Status
This article shows how to test each endpoint’s Azure AD (aka Entra ID) join status. The output can easily be used in Splunk reports and dashboards.
Machines do not always register smoothly with Azure AD. This is especially true for customers with non-persistent virtual desktops, as these types of machines must re-register with Azure AD each time they start. The script presented in this guide helps with troubleshooting by making the registration state available in Splunk.
Note: The script(s) listed in this guide are managed in vast limits’ public GitHub repository.
Collecting AAD Join Status With PowerShell From Dsregcmd
Data Source: Dsregcmd.exe
When run with the parameter Status, Dsregcmd‘s outputs a lot of information. Below is the output cropped to the data we are interested in:
+----------------------------------------------------------------------+
| Device State |
+----------------------------------------------------------------------+
AzureAdJoined : YES
EnterpriseJoined : NO
DomainJoined : NO
Virtual Desktop : NOT SET
Device Name : MACHINE1
...
Converting Dsregcmd’s Output to a Key-Value String
We’ll use the following PowerShell script to execute Dregcmd and convert its output to the KV string format required by uberAgent custom scripts:
function Test-AzureAdJoined {
$output = & dsregcmd /status
# Check if the output contains "AzureAdJoined : YES"
return $output -match "AzureAdJoined\s+:\s+YES"
}
$AzureAdJoined = 0
$joinedToAzureAd = Test-AzureAdJoined
if ($joinedToAzureAd) {
$AzureAdJoined = 1
}
# Build the output hash
$Output = @{
'AzureAdJoined' = $AzureAdJoined
}
# Finally, write the hash to stdout. The output will be picked up by uberAgent.
Write-Output $($Output.Keys.ForEach({"$_=$($Output.$_)"}) -join ' ')
The script’s output looks like this:
AzureAdJoined=1
Configuring uberAgent to Run the Script
Deploy the script to a directory on your endpoints. In this example, we’re storing it in C:\Program Files\vast limits\uberAgent\scripts as Get-AzureAdJoinStatus.ps1.
Create a new timer in uberAgent’s configuration. With the settings shown below, the script is executed one hour after uberAgent is started to give the registration process enough time, and then once every 24 hours.
[Timer]
Name = AzureAdJoinStatus
Interval = 86400000
Start delay = 3600000
Persist interval = true
Script = powershell.exe -executionpolicy bypass -file "C:\Program Files\vast limits\uberAgent\Scripts\Get-AzureAdJoinStatus.ps1"
ScriptContext = Session0AsSystem
Restart the agent to start collecting data.
Splunk It!
Once the data is in Splunk, you can list the incoming event data as follows:
index=uberagent sourcetype="uberAgent:Script:AzureAdJoinStatus"
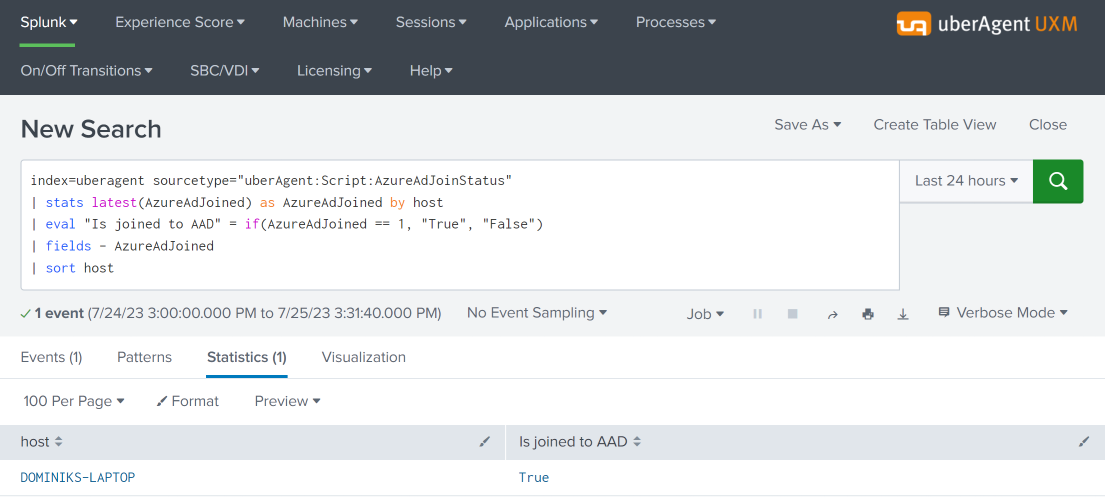
To generate a report, use a Splunk search like the following:
index=uberagent sourcetype="uberAgent:Script:AzureAdJoinStatus"
| stats latest(AzureAdJoined) as AzureAdJoined by host
| eval "Is joined to AAD" = if(AzureAdJoined == 1, "True", "False")
| fields - AzureAdJoined
| sort host
The above Splunk search creates a table with the latest AAD join status per endpoint (host in Splunk terminology):