uberAgent in the Helpdesk Pt. 4 – The Security Score
The previous posts in this series showed how uberAgent UXM enables help desk engineers to improve the digital experiences of your employees. Today, we explain how uberAgent ESA’s Security Score helps to do the same in the field of IT security.
We recommend reading the articles of the series in the following order:
- uberAgent in the Helpdesk Pt. 1 – The Helpdesk App
- uberAgent in the Helpdesk Pt. 2 – The Experience Score Overview
- uberAgent in the Helpdesk Pt. 3 – The Score Dashboards
- uberAgent in the Helpdesk Pt. 4 – The Security Score (this article)
Two Data Sources, One Dashboard
We wanted to enable customers to identify their environment’s security status by just looking at the scores with their color scheme. That’s why we introduced the all-new security score in uberAgent ESA 7.1. A dashboard, aptly titled Security Score, combines uberAgent ESA’s two main data sources into a single scoring system.
On the dashboard, we adopted the proven structure and visualization of UXM’s main dashboard, Experience Score Overview. The Security Score dashboard thus is to uberAgent ESA, what the Experience Score Overview dashboard is to uberAgent UXM.
Threat Detection Engine
The first security score data source is uberAgent’s Threat Detection Engine (TDE). TDE constantly checks monitored endpoints for risky or dangerous activity. Customers can use our comprehensive TDE ruleset right out of the box. However, they’re welcome to add their own rules or customize ours to suit their needs. Rules are written in our own uberAgent query language, uAQL, which combines the best elements of SQL and popular scripting languages. If you prefer writing rules in an editor, you should check out uAQL Studio, which is our online tool to learn, build, and test uberAgent ESA Threat Detection rules.
Isn’t Sysmon Doing the Same?
Sysmon, part of Microsoft Sysinternals suite of tools, is a monitoring and logging agent. It was created to identify malicious or anomalous activity and help IT teams understand how attackers and malware operate on company networks.
As you can see from this brief description, the purpose is very similar to that of uberAgent ESA’s Threat Detection Engine. So why consider alternatives to Sysmon? There are a few drawbacks to Sysmon, starting with the most important:
Sysmon is a tool, not a product. That means that there is no support and precious little documentation.
Sysmon also requires intensive development and testing, as it doesn’t come with a ruleset. Instead, creating and maintaining detection rules is left to the user, i.e., you. The same is true for dashboards and reports. Administrators need to create them from scratch. Finally, Sysmon stores resulting events locally, requiring a separate log forwarding agent to move the data into a centralized SIEM such as Splunk.
If you already have Sysmon deployed, our Sysmon to uberAgent ESA rule converter makes the migration painless. It translates from Sysmon’s complex XML to uberAgent’s much more readable uAQL.
If you want to learn more about uberAgent ESA as the Sysmon alternative, read here.
Stay on Top of the Latest Trends
By always having the latest rules from the leading open detection signature project, Sigma, customers can be confident that they are staying on top of new and emerging threats that could put their endpoints at risk. That’s why we pull daily updates from the project to ensure that our rules are always up to date. After pulling the updates, we convert the Sigma security signatures into TDE rules and publish them in our own GitHub repository.
Security and Compliance Inventory
Security and Compliance Inventory (SCI) is the second data source that feeds into uberAgent’s security score. SCI, introduced with uberAgent 7.1, helps identify insecure configurations in applications and operating systems. SCI is based on a modular engine whose checks and ratings can be extended by customers to include line-of-business apps, for example.
We’re focusing on the Security Score dashboard in this post. Check out this article if you want to find out more about Security and Compliance Inventory in detail.
Score Calculations
While developing the dashboard, we found that we needed to implement a custom scoring system to combine the data from our two sources, TDE and SCI. A challenge lay in the fact that TDE and SCI yield different types of results. While it’s pretty simple to work with Security and Compliance Inventory events because they come with result and risk scores, TDE events posed a challenge because they only have a risk score. So, we developed a formula that takes into account not only the actual risk score but also the number of occurrences and the number of hosts affected. If you want to learn more about how these formulas work, please read our documentation.
Working With the Security Score
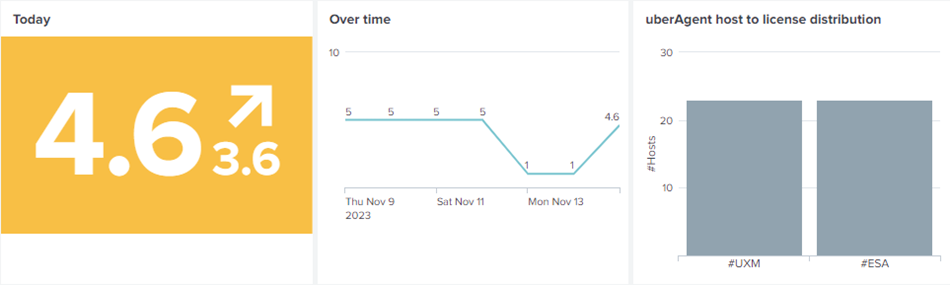
When opening the uberAgent ESA Splunk app, you start on the Security Score dashboard. The top left panel represents an overall security score for your whole environment. This score is the average of SCI’s and TDE’s scores. To its right, you can investigate how this score has changed over the past seven days. The top right panel displays whether all uberAgent UXM hosts are also equipped with uberAgent ESA.
Verify Your Machines Are Correctly Set Up
Security and compliance auditing is all about determining whether your machines, applications, and user accounts are configured securely. Of course, you don’t want to work through the raw information sent by uberAgent just to get an overview. You want to know about problems or misconfigurations as soon as they’re discovered so you can start fixing them. That is why we visualize our test results with an easy-to-understand color coding system.
The dashboard provides you with an overall score for all SCI tests. This score is derived from the scores for SCI categories such as Antivirus or PowerShell.
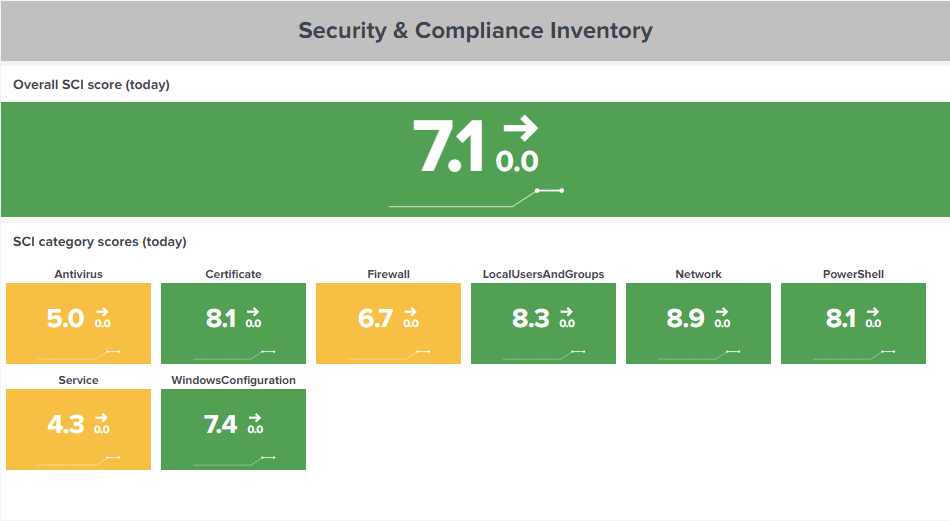
Security scores between 0 and 3.9 are considered low and are colored red, meaning action is needed. If the security score ranges from 4 to 7.9, we classify the result as medium, represented in yellow. This means that the configuration found is ok but could be more secure. An example for a medium score is a user who has Windows Hello enabled but hasn’t configured any authentication methods other than the mandatory PIN. If your configuration is good, you will see a green security score on a scale of 8 to 10. This means that the related tests yielded the expected results.
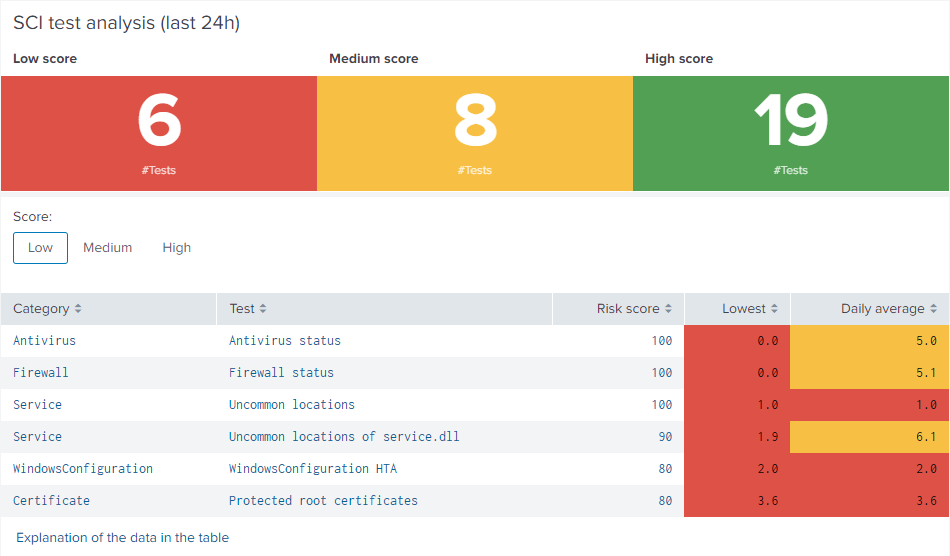
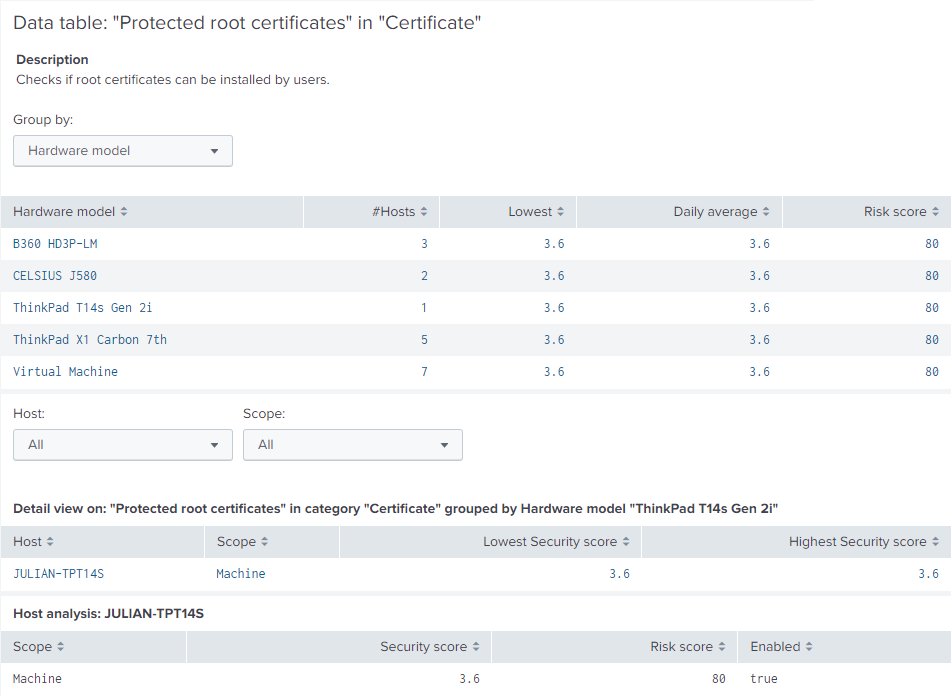
uberAgent ESA comes with a comprehensive list of tests to verify the security baseline of your endpoint fleet. Just by looking at a test’s name it may not always be obvious what a test is actually checks, so the dashboard displays a brief explanation right along with a test’s results. Selecting a specific test opens a drill-down table showing averages for all your hosts, grouped by hardware model by default. Clicking on a hardware model displays a list of all machines that belong to the selected group. After selecting a host of interest, a table displays information about the test and the endpoint’s results.
Detect Unusual Behavior
The second major data source for uberAgent ESA is our rule-based Threat Detection Engine. TDE aims to identify risky and unusual behavior on endpoints, either by applications, endpoints, or users.
As mentioned above, TDE rules are written in uberAgent’s query language, uAQL.
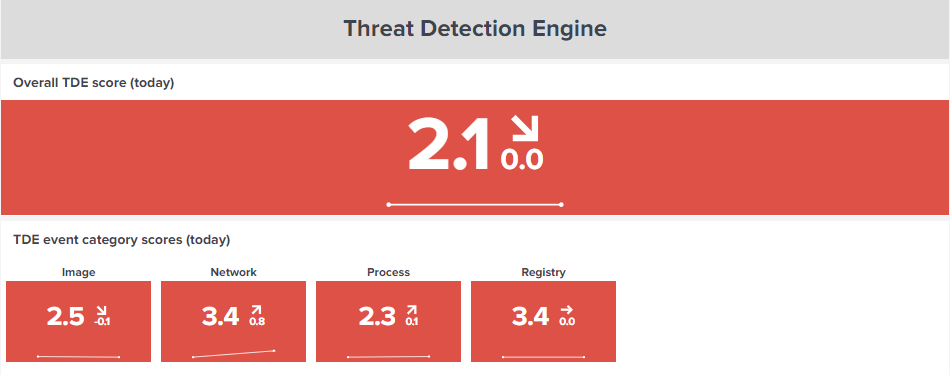
If you want to investigate a particular TDE rule tag, click on the item of interest in the TDE tag analysis panel.
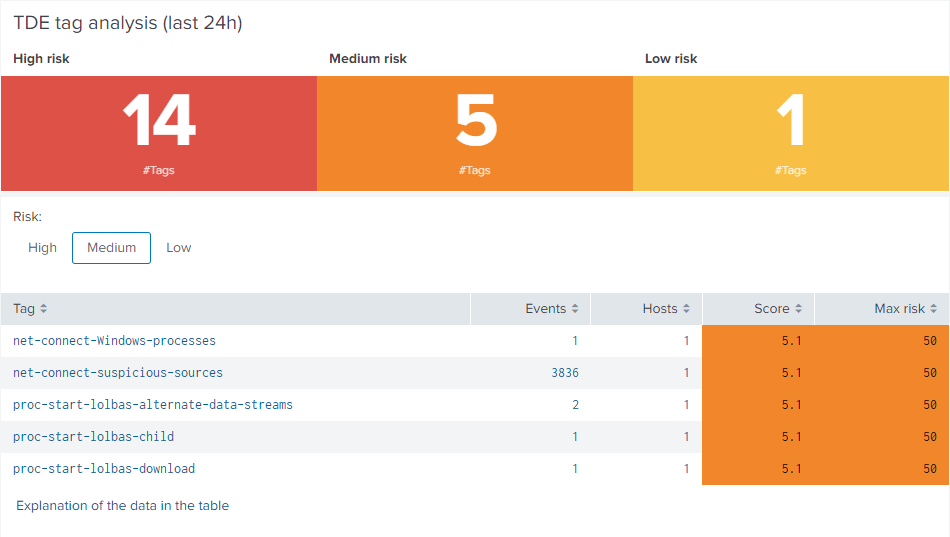
Splunk now takes you to uberAgent’s Threat Detection Events dashboard which is dedicated to analyzing TDE events in detail. It provides you with all the necessary information for further analysis, such as when and how often the events occurred, how many hosts and users are affected, and much more.
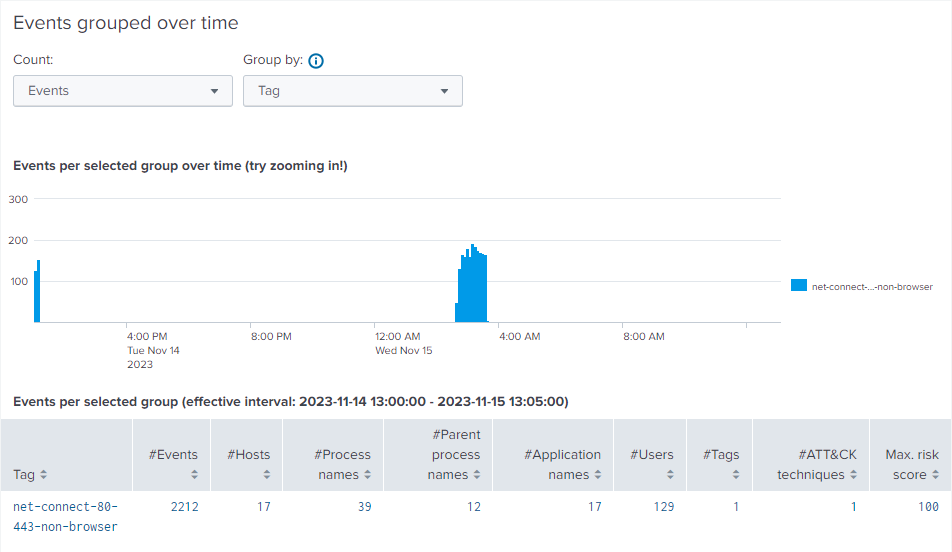
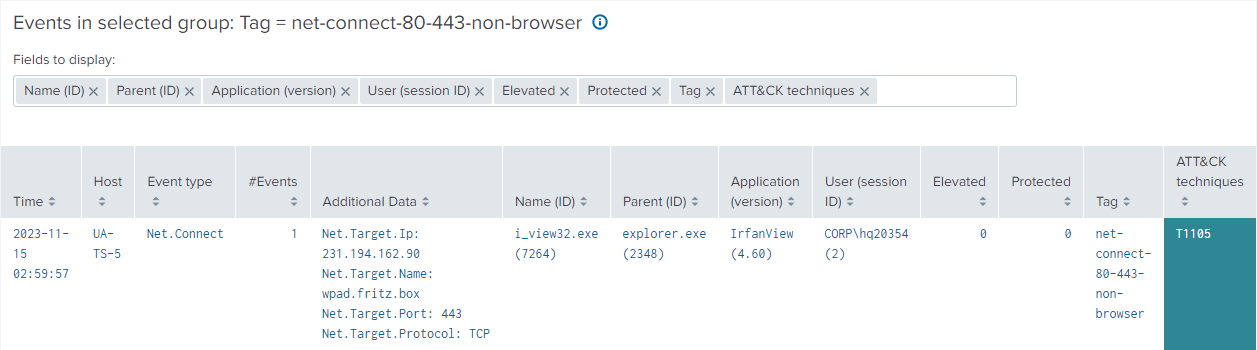
Once you select a tag in the overview table, the dashboard reveals detailed information about events matching the selected tag.
Suppose we’re looking at an event where an application was connected to the internet, the additional data field displays information about the target and the used protocol and port.
How the Security Score Helps
The Security Score dashboard helps you assess the security configuration of your environment by providing combined ratings from ESA’s two key data sources: Threat Detection Engine and Security & Compliance Inventory.
The dashboard empowers you to verify that everything is set up correctly and securely with Security and Compliance Inventory and helps you analyze user, application, and machine behavior for anomalies with Threat Detection Engine. Drill-down capabilities allow you to view actual SCI test results, while TDE event insights are available on a dedicated dashboard.
At this point, we’d like to thank you for reading our blog post series about uberAgent in the helpdesk, as this article concludes the series.
If you’re using uberAgent in your helpdesk and would like to share your experiences with us, we’d be more than happy to hear more about your use cases.
About uberAgent
The uberAgent product family offers innovative digital employee experience monitoring and endpoint security analytics for Windows and macOS.
uberAgent UXM highlights include detailed information about boot and logon duration, application unresponsiveness detection, network reliability drill-downs, process startup duration, application usage metering, browser performance, web app metrics, and Citrix insights. All these varied aspects of system performance and reliability are smartly brought together in the Experience Score dashboard.
uberAgent ESA excels with a sophisticated Threat Detection Engine, endpoint security & compliance rating, the uAQL query language, detection of risky activity, DNS query monitoring, hash calculation, registry monitoring, and Authenticode signature verification. uberAgent ESA comes with Sysmon and Sigma rule converters, a graphical rule editor, and uses a simple yet powerful query language instead of XML.
About vast limits
vast limits GmbH is the company behind uberAgent, the innovative digital employee experience monitoring and endpoint security analytics product. vast limits’ customer list includes organizations from industries like finance, healthcare, professional services, and education, ranging from medium-sized businesses to global enterprises. vast limits’ network of qualified solution partners ensures best-in-class service and support anywhere in the world.


