Documenting Applied Computer GPOs
Managing thousands of machines is a tough job for which many organizations are using Group Policy. If you are familiar with uberAgent you may know that it lists GPOs that are applied during user logon. Computer policies, on the other hand, are not part of uberAgent’s regular feature set. However, that can easily be remedied with the help of uberAgent’s custom script functionality. This article shows how.
The scripts listed in this guide are managed in vast limits’ public GitHub repository.
Listing Applied Machine Policies
In a nutshell, the uberAgent custom scripts feature executes any script you like and sends the output to Splunk. This works with any scripting engine, of course. In this case, we used PowerShell.
The following script lists all applied machine policies.
# We need a temporary XML file to store the data
$OutputFile = "C:\Windows\Temp\TempGPOExport.xml"
# If the file exists delete it
If (Test-Path $OutputFile)
{
Remove-Item $OutputFile -Force
}
# Run gpresult and store the result in the temporary xml file
gpresult.exe /Scope Computer /X $OutputFile /F
# Read the xml file
[xml]$XML = Get-Content $OutputFile
# Get the names of all GPOs
$GPOs = ($XML.Rsop.ComputerResults.GPO).Name | Sort-Object
# Remove the temporary file
Remove-Item $OutputFile -Force
# Join all GPOs to a long string
$GPOs = $GPOs -join ';'
# Write the output. uberAgent will pick this up.
Write-Output "MachineGPOs=`"$GPOs`""Save the script somewhere. For this example, we save the script as C:\Program Files\vast limits\uberAgent\Scripts\Get-MachineGPOs.ps1.
Configure uberAgent to Run the Script
Create a new timer in uberAgent’s configuration. With the settings shown below, the script will be executed once per day.
[Timer]
Name = Get-MachineGPOs
Interval = 86400000
Start delay = 600000
Persist interval = true
Thread priority = background
Script = powershell.exe -executionpolicy bypass -file "C:\Program Files\vast limits\uberAgent\Scripts\Get-MachineGPOs.ps1"
ScriptContext = Session0AsSystemSplunk it!
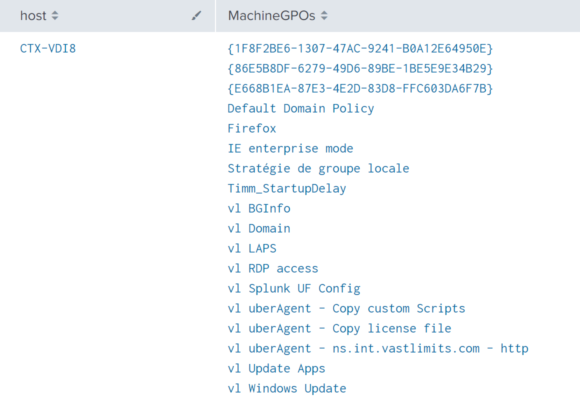
Once the data is in Splunk it can be used to document the applied computer GPOs. Run the following search to list all group policy objects per machine.
index = `uberAgent_index` sourcetype = "\"uberAgent:Script:Get-MachineGPOs\""
| stats
latest(MachineGPOs) as MachineGPOs
by host
| eval MachineGPOs = split(MachineGPOs,";")
| table
host
MachineGPOsThe results from the above search look like this: