MITRE ATT&CK Integration
MITRE ATT&CK
The MITRE ATT&CK® framework is a knowledge base of adversary tactics and techniques based on real-world observations of cybersecurity threats. With the help of ATT&CK, different stakeholders (offense, defense, SOCs, third-party vendors, and so on) can speak the same language to describe attacks on enterprise IT and mobile devices. While there are other similar frameworks available, ATT&CK is the de-facto industry standard.
Integration With uberAgent ESA
When an uberAgent ESA Threat Detection rule matches suspicious activity, uberAgent’s endpoint agent sends an event to its configured SIEM backend. uberAgent annotates Threat Detection events with ATT&CK technique IDs.
Annotations are part of the ESA Threat Detection rule specification. Implementation details can be found here. Below is a rule sample:
[ActivityMonitoringRule]
# Detects suspicious DNS queries known from Cobalt Strike beacons
RuleName = Cobalt Strike DNS Beaconing
EventType = Dns.Query
Tag = cobalt-strike-dns-beaconing
RiskScore = 100
Annotation = {"mitre_attack": ["T1071", "T1071.004"]}
Query = (Dns.QueryRequest like r"aaa.stage.%" or Dns.QueryRequest like r"post.1%")
GenericProperty1 = Dns.QueryRequest
GenericProperty2 = Dns.QueryResponseVisualization
The uberAgent ESA Splunk app processes the Threat Detection events with technique ID annotations and adds context like the technique’s name, its description and detection, and the URL to the technique on the MITRE website.
This processed information is visualized in the Threat Detection Events dashboard. In the screenshot below you can see the number of events by technique ID, and the distribution of events by ID over time.
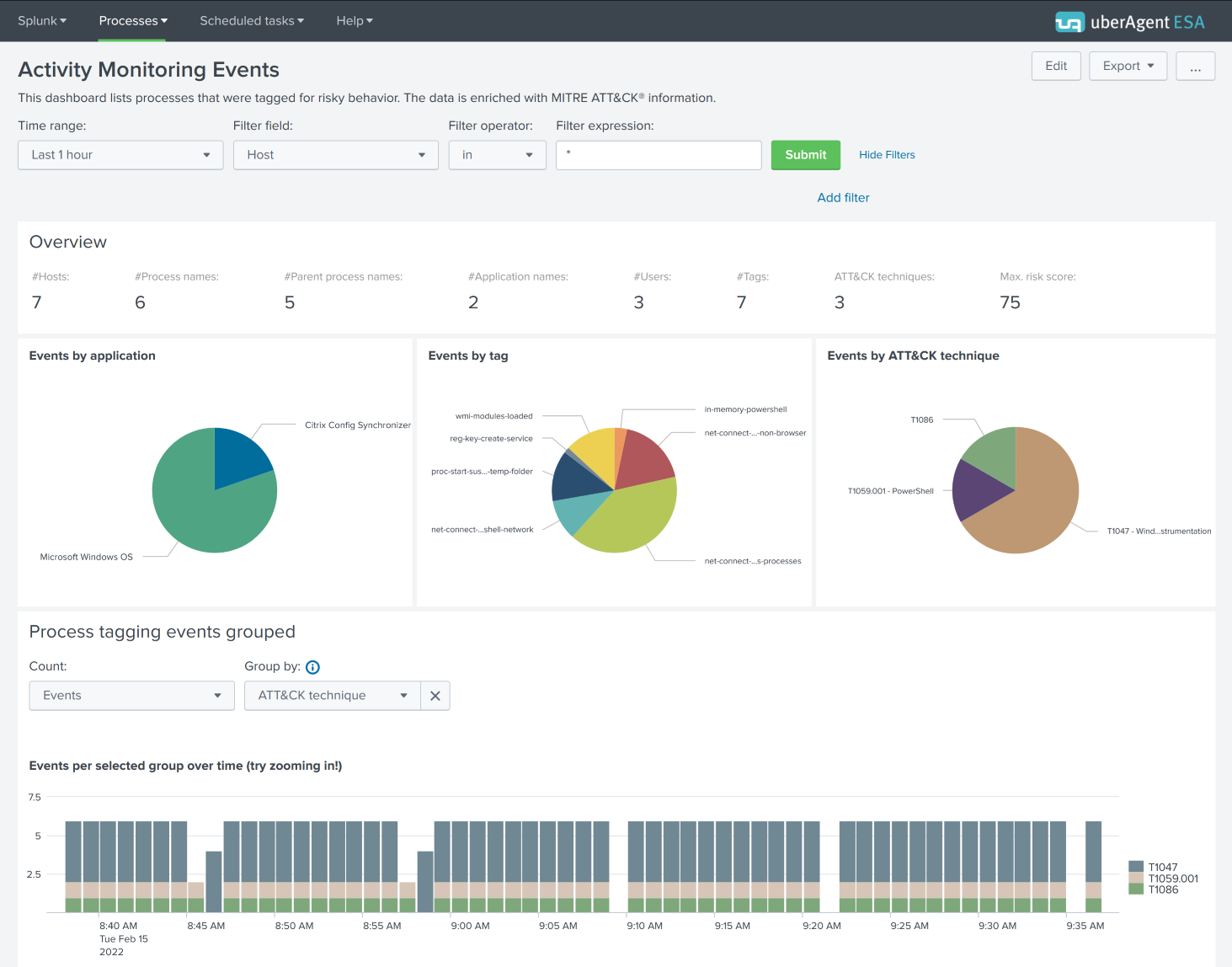
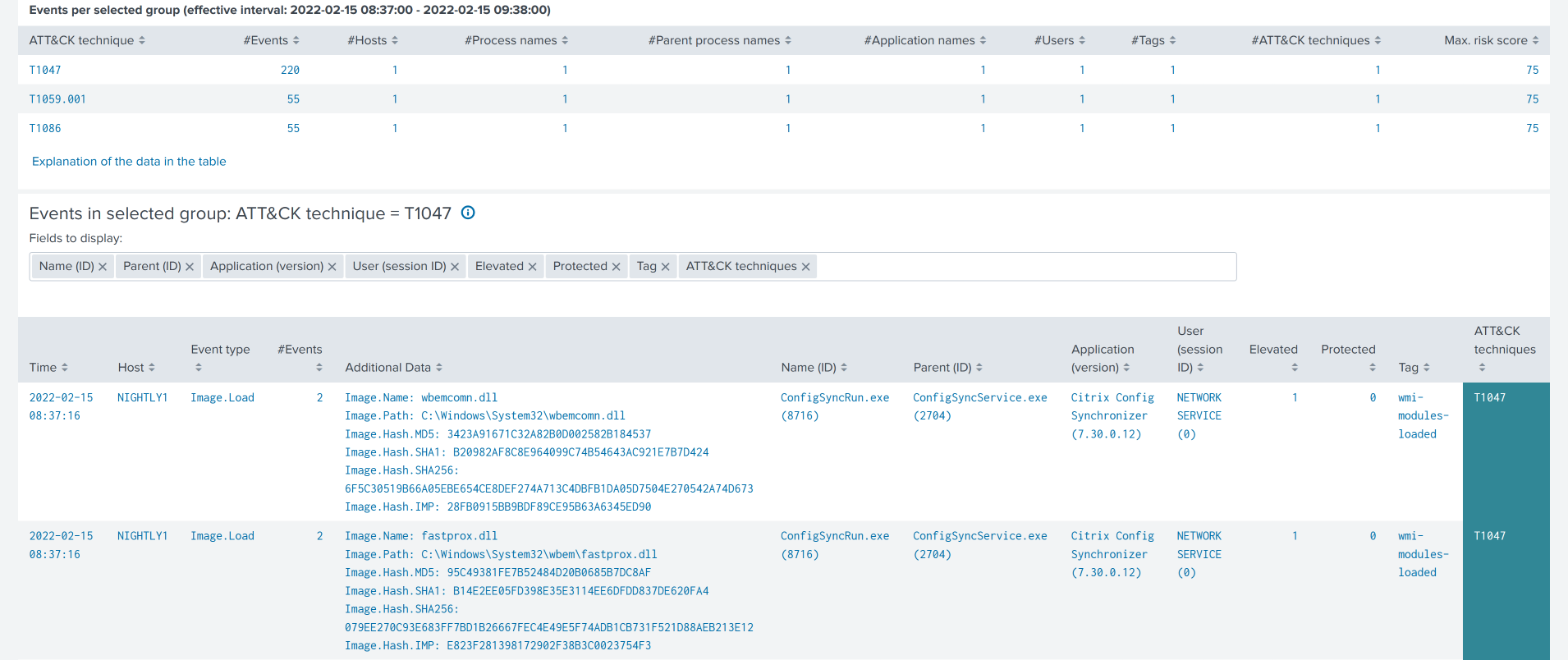
The further you scroll down the more details you get. The first table in the screenshot below shows details for each technique. A click on a technique row lists all events where the technique was detected in the second table in the screenshot below.
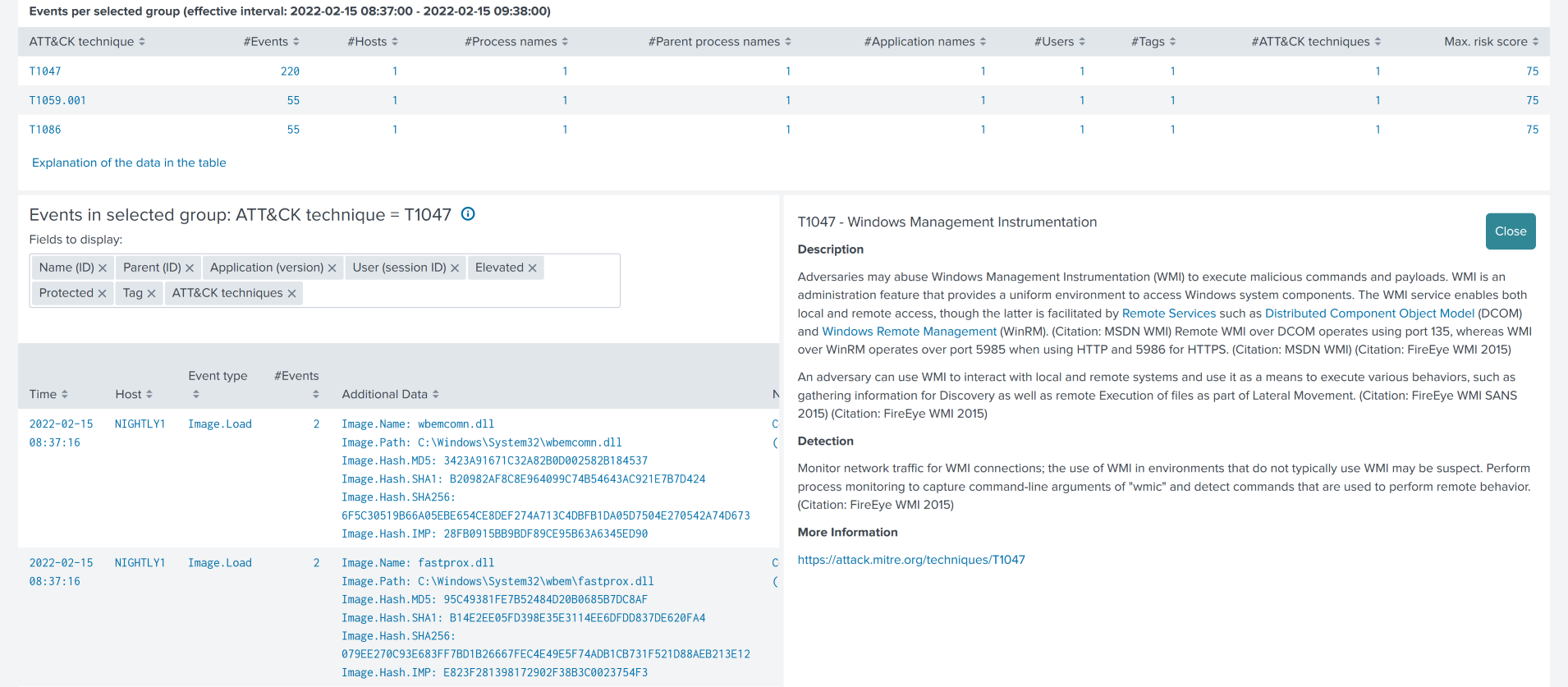
Note that the rightmost column ATT&CK techniques is highlighted in blue. When you click on it you get detailed ATT&CK information on the technique ID in a pop-up.
Installation
The ATT&CK integration is enabled by default. You don’t need to do anything except install the uberAgent ESA Splunk app on your Splunk search heads. The installation is documented here.
Keeping ATT&CK Up-to-Date
Every uberAgent release includes the latest ATT&CK information. If you notice that MITRE made changes to their ATT&CK framework and want the updated data in Splunk, you have two options:
- Wait for the next uberAgent version and update the ESA Splunk app
- Update the CSV file for the ATT&CK Splunk lookup manually
- The current CSV is always accessible in our GitHub repository. Download the file
annotation_mitre_attack.csvfrom there. - Replace the file in
$SPLUNK_HOME/etc/apps/uberAgent_ESA/lookups - Restart Splunk
- The current CSV is always accessible in our GitHub repository. Download the file
- Context: in the year 2021, MITRE made five changes to the source
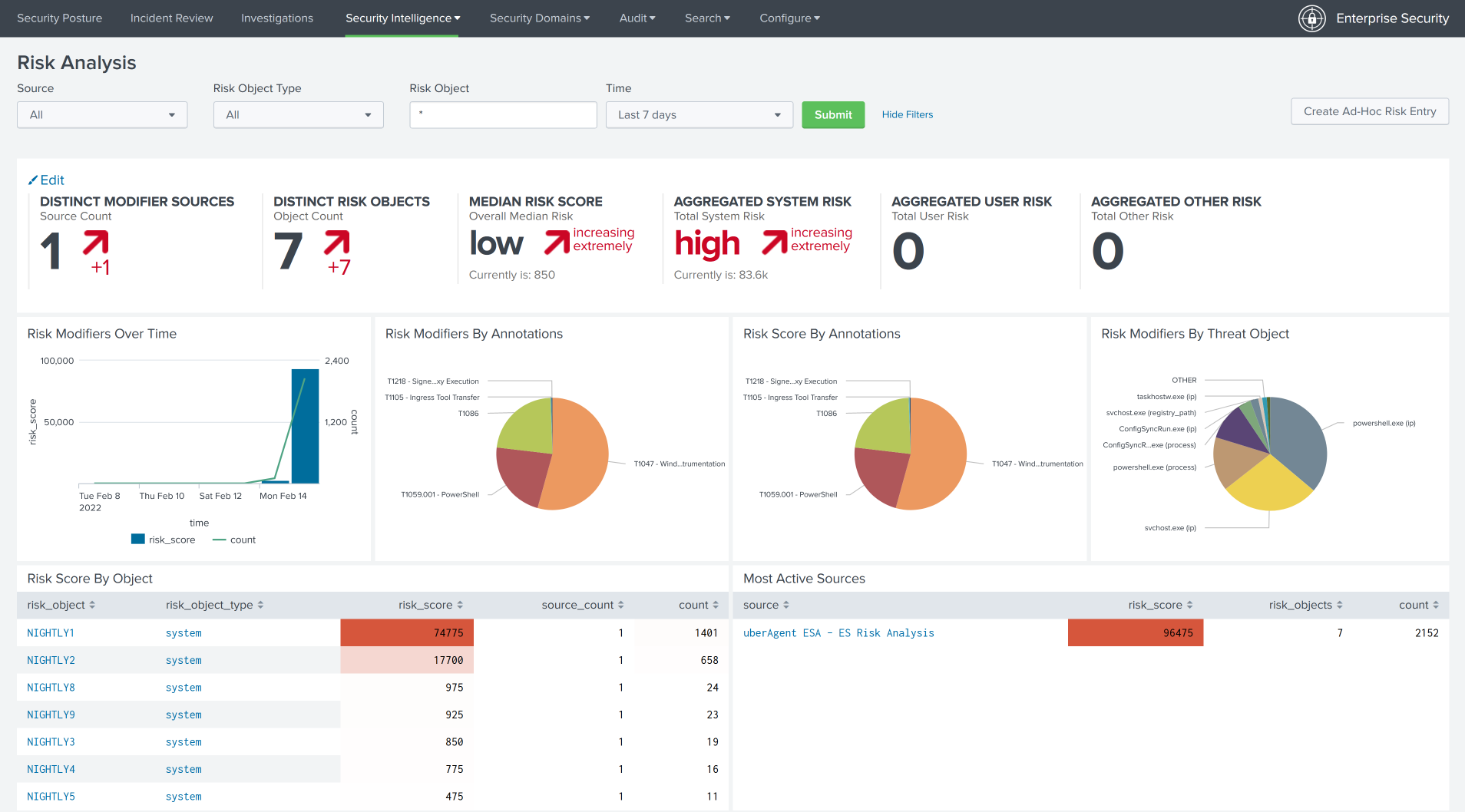
uberAgent ESA and Splunk Enterprise Security
Splunk Enterprise Security also has an ATT&CK integration and uberAgent integrates with ES, too. Below is a short summary of both integrations to avoid confusion.
uberAgent MITRE ATT&CK Data in uberAgent ESA Dashboards
The uberAgent ESA Splunk app visualizes the data collected by uberAgent’s endpoint agents. The uberAgent ESA Splunk app is compatible with Splunk Enterprise and Cloud. It has an ATT&CK integration built-in that can be used without the need to purchase Splunk Enterprise Security.
Use it when:
- You don’t have Splunk Enterprise Security
- You only need ATT&CK and no other cybersecurity framework
uberAgent MITRE ATT&CK Data in Splunk Enterprise Security
Splunk Enterprise Security is a paid premium app developed by Splunk that needs to be licensed on top of Splunk Enterprise or Cloud. It comes with support for multiple cybersecurity frameworks, ATT&CK is one of them. If you are an ES customer you may want to install the uberAgent ESA ES companion app to enjoy the benefits of uberAgent ESA data in Enterprise Security, enriched with data from cybersecurity frameworks (more information).
Use it when:
- You have Splunk Enterprise Security
- You need more cybersecurity frameworks than ATT&CK
Note: in this scenario, you can use both the uberAgent ESA app and Splunk’s Enterprise Security dashboards.