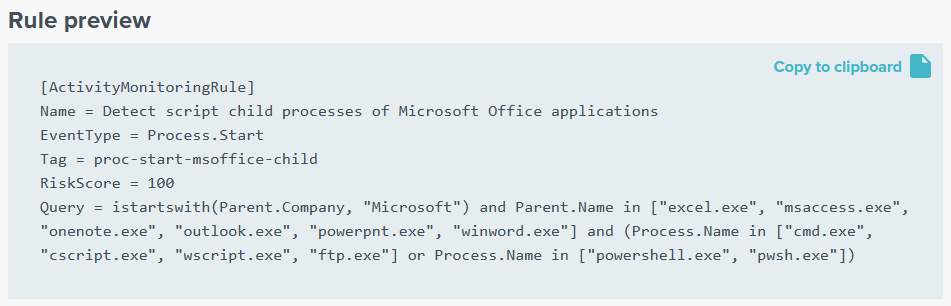
Rule Editor: uAQL Studio
uAQL Studio is a free online tool to learn, build and test uberAgent ESA Threat Detection rules.
Quickstart
Follow these steps to get started with uAQL Studio quickly:
- Open uAQL Studio in a new browser tab
- Select an event type
- Add events to test the uAQL query your going to write
- Work on your uAQL query until it matches your test events correctly
- Fill out the fields
Rule name,Tag,Risk score - Copy the rule definition from the preview pane to the clipboard and paste it into your uberAgent ESA configuration
Walkthrough
In this walkthrough, we’re building a Threat Detection rule that detects script child processes of Microsoft Office applications.
Launch uAQL Studio
Click the following link to launch uAQL Studio in a new browser tab: https://uberagent.com/uaql-studio/.
Select an Event Type
uberAgent ESA Threat Detection supports many different types of events, including process, network, registry, and DNS events. Select the Process.Start event type:
Add a Test Event
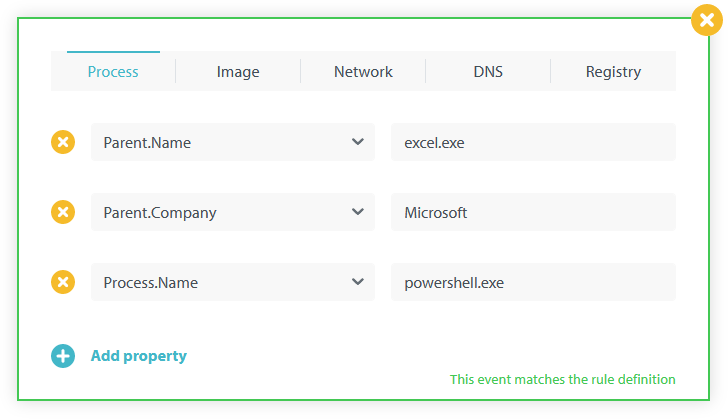
Click Add event and specify the properties of an event you want uAQL Studio to match against the uAQL query you’re going to write. Since we’re creating a rule to detect script child processes of MS Office apps we’re adding the properties of just such an event:
- Parent.Name:
excel.exe - Parent.Company:
Microsoft - Process.Name:
powershell.exe
It should look similar to this:
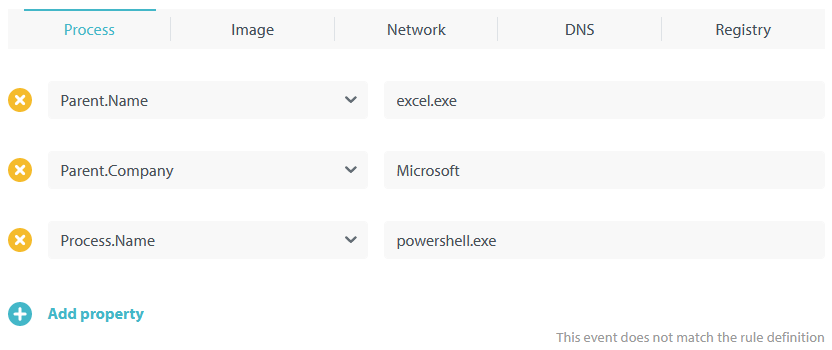
As you can see in the lower right corner of the above screenshot, at this point the test event is not matched by the rule definition (aka, the query). That is correct, of course. After all, the query is still empty!
Define the uAQL Query
Detecting Child Processes of MS Office Apps
Let’s start to work on our detection query by first creating a snippet that identifies child processes of MS Office apps. Please see the documentation for details. The following properties should work:
- the company name of the parent process needs to start with
Microsoft(which also covers “Microsoft Corporation” and variants like “Microsoft Corp.”, all of which can be found in the wild) - the parent process name must be one of the following:
excel.exe,msaccess.exe,onenote.exe,outlook.exe,powerpnt.exe,winword.exe
In uAQL code the above looks as follows:
istartswith(Parent.Company, "Microsoft") and Parent.Name in ["excel.exe", "msaccess.exe", "onenote.exe", "outlook.exe", "powerpnt.exe", "winword.exe"]
Detecting Script Processes
We define the following executables as script runtimes:
- PowerShell:
powershell.exe,pwsh.exe - Batch, VBS, miscellaneous:
cmd.exe,cscript.exe,wscript.exe,ftp.exe
In uAQL code the above looks as follows:
Process.Name in ["cmd.exe", "cscript.exe", "wscript.exe", "ftp.exe"] or Process.Name in ["powershell.exe", "pwsh.exe"]
Putting the Query Together
We can now combine the two snippets into the complete uAQL query:
istartswith(Parent.Company, "Microsoft") and Parent.Name in ["excel.exe", "msaccess.exe", "onenote.exe", "outlook.exe", "powerpnt.exe", "winword.exe"] and (Process.Name in ["cmd.exe", "cscript.exe", "wscript.exe", "ftp.exe"] or Process.Name in ["powershell.exe", "pwsh.exe"])
Paste the Query Into uAQL Studio
Copy the completed query from above and paste it into the Query field in uAQL Studio. The built-in syntax checking mechanism should show a green checkmark similar to the following:
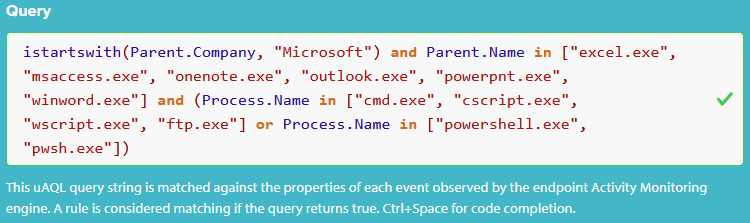
Verify the Test Event Matches
Take a look at the test event we created earlier. The green border indicates that it matches the query. The text in the lower right corner has changed to This event matches the rule definition:
Add Rule Metadata
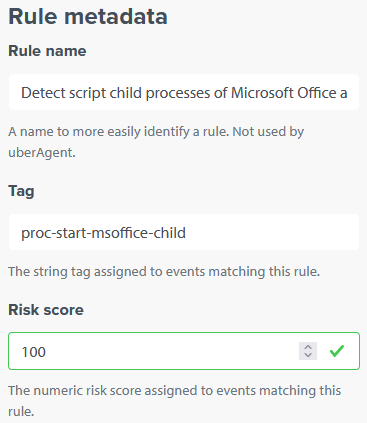
The rule definition is now complete but we need to add some metadata to make it usable with uberAgent and Splunk. Please see the documentation for details. The following values work well:
- Rule name:
Detect script child processes of Microsoft Office applications - Tag:
proc-start-msoffice-child - Risk score:
100
The UI should now look similar to the following:
Copy the Rule Definition
With this, the rule definition is complete. We can copy it from the preview pane and use it with uberAgent ESA!