Creating a List of Known Good Processes for Whitelisting
Process whitelisting is an effective remedy against many types of malware. By allowing only known-good processes to run, you ensure that potentially malicious applications are blocked no matter where they came from. The difficulty with this approach lies with the creation of the whitelist. If you miss legitimate processes, applications break. Here is how uberAgent can help.
Overview: How to Create the Process Whitelist
For the method presented here, you need a known “clean” reference system with exactly the same application set and configuration as your production systems. Do the following:
- Install uberAgent on the reference system
- Have real end-users work on the reference system for a few hours
- Run a Splunk search to generate a listing of all started processes from uberAgent’s data
- Export the process listing to CSV
- Use the CSV file as a basis for your whitelist
A more detailed explanation of these steps follows below.
uberAgent Data Collection
Follow these instructions to get uberAgent installed on your reference system. It should not take long. As soon as the agent is running and sending data to Splunk, a wealth of high-quality information is waiting to be put to use.
In this case, we are only going to work with a tiny fraction of all that is available. Whenever a process is started, uberAgent collects the following information and tags it with the sourcetype uberAgent:Process:ProcessStartup in Splunk:
- Process name
- User account and domain name
- Process startup duration
- Process startup disk IOPS
- Application name
- Process ID of the process being started
- Process ID of the process’ parent
- RDS session ID
- Process GUID*
- Session GUID*
- Process name of the process’ parent*
- Full path to the process being started*
- Commandline of the process being started*
*) The fields marked with asterisks are only available once the optional configuration setting EnableExtendedInfo has been enabled
Generating the Process Listing
With uberAgent recording the reference system’s process starts in Splunk all we need to do in order to generate the whitelist is to run a Splunk search. If you have EnableExtendedInfo enabled, you can get process names as well as the full path to each process like this:
index=uberagent sourcetype=uberAgent:Process:ProcessStartup | stats values(AppName) as "App name(s)" count as "Start count" by ProcName ProcPath | rename ProcName as "Process name" ProcPath as "Process Path"
If you do not have EnableExtendedInfo enabled, you can get process names:
index=uberagent sourcetype=uberAgent:Process:ProcessStartup | stats values(AppName) as "App name(s)" count as "Start count" by ProcName | rename ProcName as "Process name"
Please make sure a reasonable time range is selected (the last four hours might be a good starting point). The result should look similar to the following:
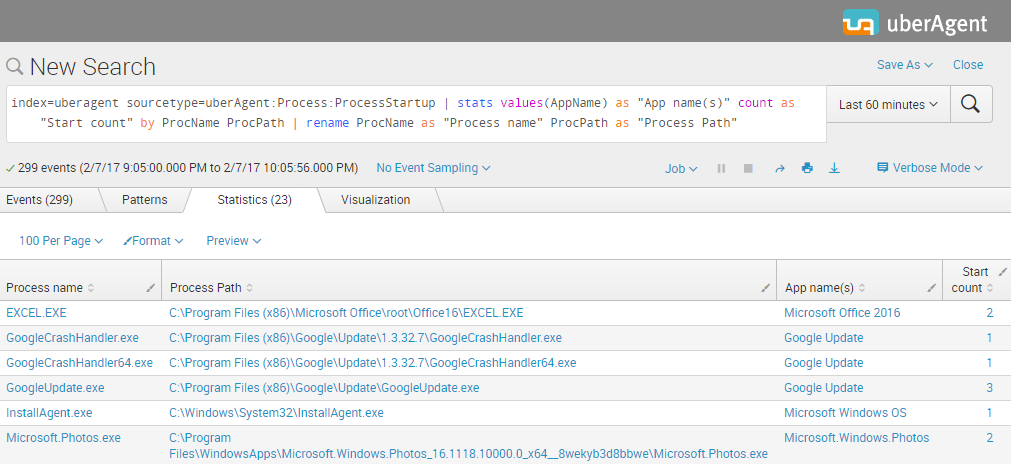
As you can see in the screenshot above we get a list with the columns: Process name, Process path, App name(s) and Start count. Let’s export it to CSV by clicking the Export button:
Using the Process Whitelist
As you have seen it just took a few simple steps to generate a comprehensive CSV export of all processes that were started on a reference system. Such a list is a great starting point for whitelisting allowed processes. As a next step, we recommend you verify the processes on the list and then import them into your security product. Let us know how it goes!
About uberAgent
The uberAgent product family offers innovative digital employee experience monitoring and endpoint security analytics for Windows and macOS.
uberAgent UXM highlights include detailed information about boot and logon duration, application unresponsiveness detection, network reliability drill-downs, process startup duration, application usage metering, browser performance, web app metrics, and Citrix insights. All these varied aspects of system performance and reliability are smartly brought together in the Experience Score dashboard.
uberAgent ESA excels with a sophisticated Threat Detection Engine, endpoint security & compliance rating, the uAQL query language, detection of risky activity, DNS query monitoring, hash calculation, registry monitoring, and Authenticode signature verification. uberAgent ESA comes with Sysmon and Sigma rule converters, a graphical rule editor, and uses a simple yet powerful query language instead of XML.
About vast limits
vast limits GmbH is the company behind uberAgent, the innovative digital employee experience monitoring and endpoint security analytics product. vast limits’ customer list includes organizations from industries like finance, healthcare, professional services, and education, ranging from medium-sized businesses to global enterprises. vast limits’ network of qualified solution partners ensures best-in-class service and support anywhere in the world.


