Building uberAgent ESA: Scheduled Task Monitoring
This post is part of a series about the new uberAgent Endpoint Security Analytics (ESA) product. uberAgent ESA aims to provide deep security visibility. It is complemented by uberAgent UXM, our user experience monitoring solution, which adds rich context and metadata.
Scheduled tasks are fantastic for hiding malware. There are multiple reasons for that: every Windows PC has a huge number of tasks, all of which are completely undocumented, there is no authentication mechanism for “good” tasks, and essential information is not available in the UI. Let us explore those caveats in more detail.
Issues With Scheduled Tasks
Huge Number of Tasks, All Undocumented
The machine I am writing this on has a total number of 221 scheduled tasks spread across 127 folders. Most of these tasks came with the Windows operating system, but some were added by applications or drivers. Microsoft Office 365, for example, installs the following tasks:
- Office Automatic Updates 2.0
- Office ClickToRun Service Monitor
- Office Feature Updates
- Office Feature Updates Logon
- Office Subscription Maintenance
- OfficeBackgroundTaskHandlerLogon
- OfficeBackgroundTaskHandlerRegistration
- OfficeTelemetryAgentFallBack2016
- OfficeTelemetryAgentLogOn2016
We can deduce from the names of these tasks that most of them are related to application updates and telemetry. Each task’s description field contains rudimentary information, but apart from that, these tasks are undocumented. The same is true for basically all scheduled tasks.
No Authentication Mechanism for “Good” Tasks
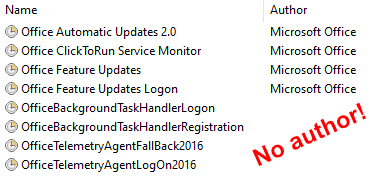
Unlike executables, scheduled tasks cannot be digitally signed. As a consequence, there is no way to verify if a task is genuine. Tasks do have an author field, but its contents can be set to anything, making it worthless for security purposes.
Nothing demonstrates that better than the Office tasks mentioned earlier. As you can see in the screenshot below, some of those tasks do not even have an author configured at all!
Essential Information Is Not Available in the UI
Scheduled tasks are all about doing something: running a tool, starting a script, invoking a component. Without any such action, a task is useless. In other words, a task’s action is by far its most important property. All the more alarming that the Task Scheduler UI in many cases does not display this essential information:
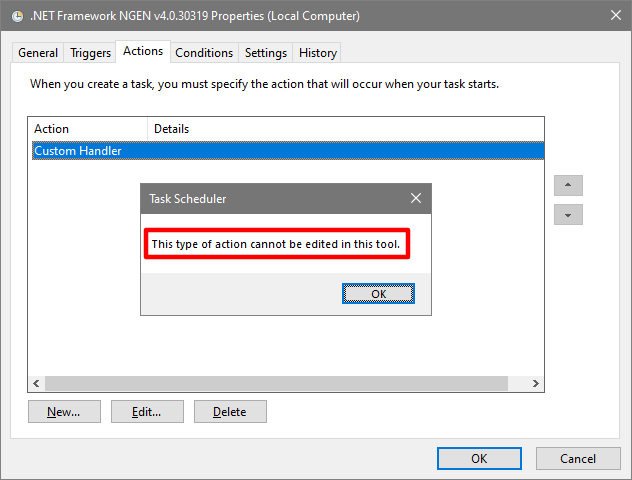
More specifically, Task Scheduler neither shows details for COM actions nor does it list properties of custom triggers. The same is true for command-line tools like schtasks.exe. Essentially, Windows turns a blind eye to scheduled tasks.
uberAgent ESA Scheduled Task Monitoring
The only solution to dealing with the weaknesses of Windows scheduled tasks is careful monitoring. uberAgent Endpoint Security Analytics (ESA) puts you in control again.
Detecting Task Creation, Update and Delete
uberAgent ESA automatically detects the relevant events in a scheduled task’s lifecycle: task creation, task change/update, and task deletion.
Full Details on Scheduled Task Triggers
Scheduled tasks have a complex architecture: each task may have several, even different triggers. A task could be triggered at machine boot, user logon, according to a schedule, or any combination of the above. There is also a huge number of undocumented custom triggers. uberAgent ESA lists all of these triggers in full detail.
Scheduled Task Actions, Unraveled
As with triggers, tasks can be configured with more than one action. Some actions, like starting a process, or sending an email are straightforward. Instantiating a COM object is not. All the more important to clearly understand exactly what is being executed.
For each COM action, uberAgent ESA not only lists the component’s CLSID but also resolves it to the actual executable hosting the component.
More Information About uberAgent ESA
See our blog post announcing uberAgent Endpoint Security Analytics for more information about uberAgent ESA. Also, follow this blog – we have more to share soon!
About uberAgent
The uberAgent product family offers innovative digital employee experience monitoring and endpoint security analytics for Windows and macOS.
uberAgent UXM highlights include detailed information about boot and logon duration, application unresponsiveness detection, network reliability drill-downs, process startup duration, application usage metering, browser performance, web app metrics, and Citrix insights. All these varied aspects of system performance and reliability are smartly brought together in the Experience Score dashboard.
uberAgent ESA excels with a sophisticated Threat Detection Engine, endpoint security & compliance rating, the uAQL query language, detection of risky activity, DNS query monitoring, hash calculation, registry monitoring, and Authenticode signature verification. uberAgent ESA comes with Sysmon and Sigma rule converters, a graphical rule editor, and uses a simple yet powerful query language instead of XML.
About vast limits
vast limits GmbH is the company behind uberAgent, the innovative digital employee experience monitoring and endpoint security analytics product. vast limits’ customer list includes organizations from industries like finance, healthcare, professional services, and education, ranging from medium-sized businesses to global enterprises. vast limits’ network of qualified solution partners ensures best-in-class service and support anywhere in the world.


