Announcing uberAgent Endpoint Security Analytics
We have come a long way with uberAgent. What started out as a tool for optimizing Citrix XenApp environments evolved into a full-fledged monitoring product that covers all aspects of user experience and application performance on any Windows endpoint – and soon on macOS, too. uberAgent collects detailed inventory information, shows which applications are used when and how often, determines application reliability KPIs, finds issues with network connectivity, and much more. Such a rich data set can only be collected by closely monitoring system activity: process creation, network transmissions, and many other types of events – all of which are highly relevant in a security context, too. In fact, several of our customers are using uberAgent at least in part for security scenarios. To better support that, we are officially announcing a new product: uberAgent Endpoint Security Analytics (ESA).

The Foundation: uberAgent UXM
uberAgent ESA is built on top of our existing product, which we are renaming to uberAgent User Experience Monitoring (UXM). The reason for logically placing ESA on top of UXM becomes clear when we take a closer look at the metrics that UXM already provides:
Applications
- Automatic application identification: maps processes to applications (e.g.,
iexplore.exetoInternet Explorer) - Application inventory: tells you which apps are installed on disk
- Application usage: tells you which apps are running (typically a small subset of those installed)
- Foreground application: tells you which application the user is interacting with (just one app per session at any given point in time)
- Application startup: records process creation and app startup duration
- Application performance: resource utilization for the entire app or individual processes
All of the above works for any kind of native applications, of course, including Win32, UWP, Java, and App-V. But there is more. After all, the browser has become an OS for web apps. Where other monitoring tools only show a browser as a gigantic consumer of system resources uberAgent UXM goes several steps further by providing detailed usage and performance metrics for SaaS apps, too.
Users
- Logon and logoff activity
- Session start and end
- User account for all process or application events
- User metadata can be read from any AD attribute, registry value or environment variable
Operating system process IDs and session IDs are not useful for tracking individual instances because the IDs are reused (quickly). uberAgent solves this by generating unique IDs (GUIDs) for every process or session.
Networking
- Network connections both on the OS level and in the browser
- Network activity per application, process, and user
In addition to monitoring successful network activity, uberAgent also identifies connection attempts that fail. This greatly helps find misconfigurations or incorrect firewall rules.
UXM Summary
We are quite aware that the above metrics might make a nice security product already and we are more than happy to support such a use case with uberAgent UXM. However, until now, security was a by-product. This changes with ESA. Now we are getting serious with security.
uberAgent ESA in a Nutshell
uberAgent UXM provides rich context and metadata, while uberAgent ESA adds deep security visibility.
With the combination of ESA and UXM, you need only one agent for user experience, performance, and security. This guarantees the smallest possible footprint on the endpoint. Our technology is based on the famously efficient and reliable uberAgent UXM which has been deployed to enterprises worldwide with up to 300,000 users per organization.
Our endpoint agent supports any version of Windows, be it physical or virtual, client or server, mobile or not (and soon macOS, too).
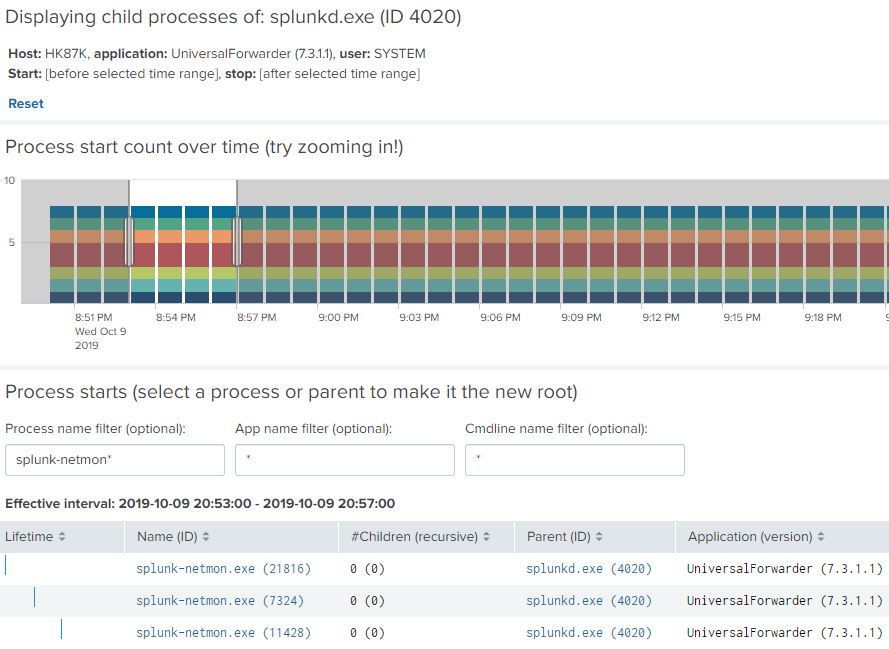
uberAgent ESA Process Tree dashboard filtered to include only splunk-netmon child processes of Splunk Universal Forwarder
uberAgent ESA Features
Process Tagging
We want to enable businesses to identify risky processes. Matching processes get a tag and a risk score, both of which can be freely chosen. As can be the way risky processes are detected, thanks to our powerful and flexible rule definition language. Process tagging rules can be organized in reusable blocks; all detection elements support regular expressions and some even a combination of regexes and environment variables.
uberAgent ESA comes with predefined rules for many common threats, including Microsoft Office child process identification, or the ability to flag processes that are started from directories standard users, or, even worse, low-integrity processes can write to. Advanced directory permission SDDL analytics are available out of the box, too.
Scheduled Tasks
Scheduled Tasks are a fantastic way to hide malware. There are multiple reasons for this. One, the Task Scheduler UI does not display important properties like COM actions or custom triggers. Two, there is a huge number of tasks on any system, all of which are completely undocumented by Microsoft or the respective third-party software vendor. Three, there is no built-in authentication method for “good” tasks.
Those challenges require careful monitoring with a tool that detects any change and collects all properties. uberAgent ESA shows new, changed or deleted scheduled tasks with all their properties, triggers, and actions. In the case of COM actions, for example, uberAgent determines the CLSID and the executable of the COM component that is targeted by the task.
Process Tree Dashboard
We mentioned earlier that uberAgent logs process creation events along with rich metadata about what exactly is being launched where and by whom. Such information can be invaluable, but it also needs to be navigable. All of the metrics collected by uberAgent are accessible through preconfigured dashboards, of course, but one of them demands some special attention. The uberAgent ESA process tree dashboard allows for comfortable navigation through complex hierarchies of even millions of parent-child process relationships, giving analysts a powerful tool that helps them understand process activities through interactive visualization.
And More…
The features described here are just a teaser of the powerful capabilities that come with uberAgent ESA. Development is still ongoing, so please bear with us. We will share more news as soon as possible.
uberAgent at Splunk .conf
Make sure to attend our Splunk .conf session SECS2534 to learn more about uberAgent Endpoint Security Analytics. And come to our booth #108, of course. Do not miss your chance to talk to uberAgent’s developers and engineers!
About uberAgent
The uberAgent product family offers innovative digital employee experience monitoring and endpoint security analytics for Windows and macOS.
uberAgent UXM highlights include detailed information about boot and logon duration, application unresponsiveness detection, network reliability drill-downs, process startup duration, application usage metering, browser performance, web app metrics, and Citrix insights. All these varied aspects of system performance and reliability are smartly brought together in the Experience Score dashboard.
uberAgent ESA excels with a sophisticated Threat Detection Engine, endpoint security & compliance rating, the uAQL query language, detection of risky activity, DNS query monitoring, hash calculation, registry monitoring, and Authenticode signature verification. uberAgent ESA comes with Sysmon and Sigma rule converters, a graphical rule editor, and uses a simple yet powerful query language instead of XML.
About vast limits
vast limits GmbH is the company behind uberAgent, the innovative digital employee experience monitoring and endpoint security analytics product. vast limits’ customer list includes organizations from industries like finance, healthcare, professional services, and education, ranging from medium-sized businesses to global enterprises. vast limits’ network of qualified solution partners ensures best-in-class service and support anywhere in the world.


