User Session Script Collecting Custom Metrics (Citrix ICA RTT)
uberAgent is often used in conjunction with Universal Forwarder, Splunk’s generic agent that monitors logs and collects the output from custom scripts. The combination of the two agents is a powerful one, as it allows customers to add any metric they require to uberAgent’s already rich dataset.
However, running two agents side by side has drawbacks, too: the administrative overhead increases as do the hardware resources required on the endpoints.
As of uberAgent 4.1, there exists an attractive alternative: what started out with the intention of providing a way of collecting custom metrics from individual user sessions turned into a generic script execution engine. It runs any type of script at any desired interval, either per machine or per user session (documentation).
Example: Querying WMI Data Using a PowerShell Script
This example shows how to collect the ICA RTT metric in every user session by way of a custom script running every 30s. The ICA protocol round trip time (RTT) is an important metric supplementing uberAgent’s remoting protocol latency in Citrix XenApp / XenDesktop environments. You can find a detailed description of the ICA RTT metric here.
The following PowerShell script queries the ICA RTT as a property of a WMI class:
$Citrix_Euem_RoundTrip = Get-WmiObject -Namespace root\Citrix\euem -Class Citrix_Euem_RoundTrip
$CurrentSessionID = [System.Diagnostics.Process]::GetCurrentProcess().SessionId
foreach ($Session in $Citrix_Euem_RoundTrip)
{
if ($Session.SessionID -eq $CurrentSessionID)
{
[Hashtable]$Output = @{
'RoundtripTime'=$($Session.RoundtripTime)
'SessionID'=$($Session.SessionID)
'SessionUser'=[System.Security.Principal.WindowsIdentity]::GetCurrent().Name
}
Write-Output $($Output.Keys.ForEach({"$_=$($Output.$_)"}) -join ' ')
}
}
All properties (SessionUser, SessionID and RoundtripTime) are written to stdout as key-value pairs:
SessionUser=AD\timmtest02 SessionID=5 RoundtripTime=28
This script (named Citrix_Euem_RoundTrip.ps1) is located in the %ProgramFiles%\vast limits\uberAgent\Scripts directory on the endpoint.
I configured the script execution as follows in uberAgent’s configuration:
############################################
# Timer 10
############################################
[Timer]
Name = PowerShell Citrix Euem RoundTrip
Interval = 30000
Script = powershell.exe -executionpolicy bypass -file "C:\Program Files\vast limits\uberAgent\Scripts\Citrix_Euem_RoundTrip.ps1"
ScriptContext = UserSessionAsUser
As you can see, this script is executed every 30 seconds (30,000 milliseconds) as user inside every interactive session.
The Splunk search results look as follows:
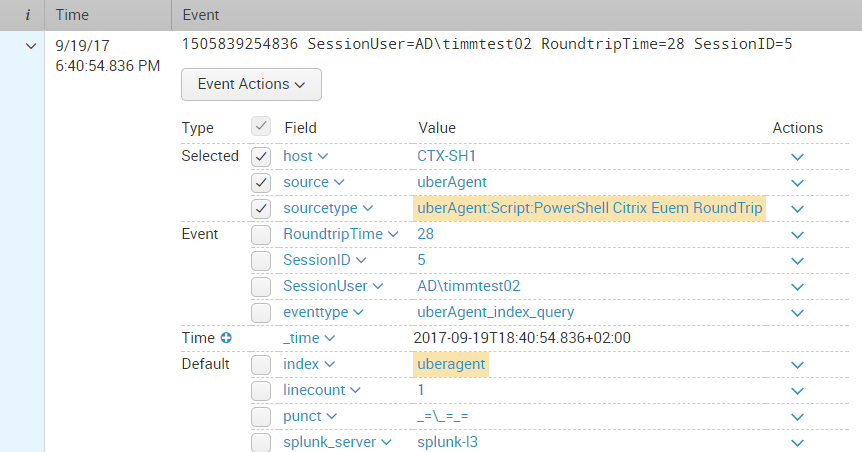
By default, all collected data is sent to the Splunk index uberagent. The Splunk sourcetype used for the script’s output is a concatenation of uberAgent:Script: and the timer name specified in uberAgent’s configuration.
About uberAgent
The uberAgent product family offers innovative digital employee experience monitoring and endpoint security analytics for Windows and macOS.
uberAgent UXM highlights include detailed information about boot and logon duration, application unresponsiveness detection, network reliability drill-downs, process startup duration, application usage metering, browser performance, web app metrics, and Citrix insights. All these varied aspects of system performance and reliability are smartly brought together in the Experience Score dashboard.
uberAgent ESA excels with a sophisticated Threat Detection Engine, endpoint security & compliance rating, the uAQL query language, detection of risky activity, DNS query monitoring, hash calculation, registry monitoring, and Authenticode signature verification. uberAgent ESA comes with Sysmon and Sigma rule converters, a graphical rule editor, and uses a simple yet powerful query language instead of XML.
About vast limits
vast limits GmbH is the company behind uberAgent, the innovative digital employee experience monitoring and endpoint security analytics product. vast limits’ customer list includes organizations from industries like finance, healthcare, professional services, and education, ranging from medium-sized businesses to global enterprises. vast limits’ network of qualified solution partners ensures best-in-class service and support anywhere in the world.


