uberAgent 7.1 Preview: Endpoint Security Testing & Rating With Security & Compliance Inventory
While we’re working on version 7.1 of our digital employee experience monitoring & endpoint security analytics products uberAgent UXM and uberAgent ESA, let’s take a look at an exciting new ESA feature: Security & Compliance Inventory.
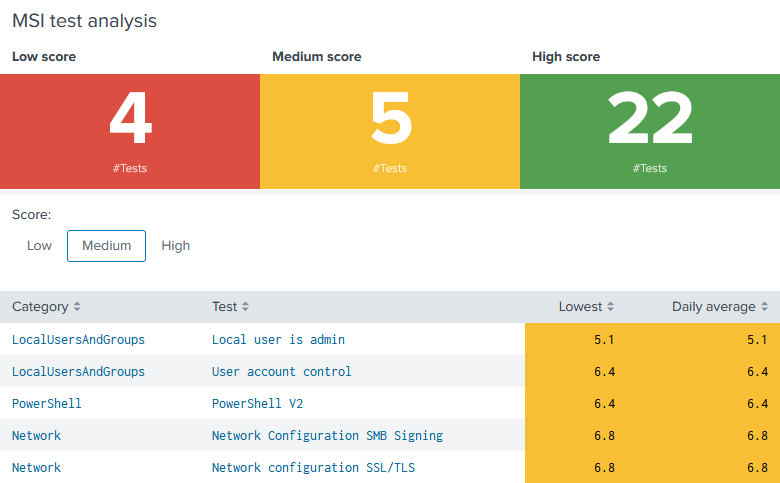
What is Security & Compliance Inventory?
uberAgent Security & Compliance Inventory is a testing and rating framework that checks the attack surface of your operating systems and applications. The test results are used to calculate security scores that pinpoint configuration and security hardening weaknesses.
Let’s dive into the innovative features of uberAgent Security & Compliance Inventory (SCI).
Comprehensive Suite of Security Tests
uberAgent ESA comes with a comprehensive suite of SCI tests that cover a broad range of attack scenarios, including, but not limited to, the following.
Man-in-the-Middle Attacks
Compromised root certificates enable man-in-the-middle attacks: if attackers gain access to the private key of a root certificate that is trusted by the target endpoint, they can intercept and re-encrypt HTTPS data streams. uberAgent ESA helps detect these threats with tests such as the following (excerpt):
- OS root certificate updates. Are automatic updates of the OS root certificates enabled? If so, when was the last update check performed?
- Additional root certificates. Are there any root certificates that do not originate from the OS vendor?
PowerShell Abuse
Due to the rich capabilities of the PowerShell scripting language, attackers often use PowerShell scripts in their attack chains. It also helps threat actors – a lot – that PowerShell is included with the Windows OS and, therefore, doesn’t require additional downloads or executables. uberAgent ESA helps tighten PowerShell security with tests such as the following (excerpt):
- Is PowerShell v2 disabled? The obsolete version 2 of PowerShell is still included with current versions of Windows. Although it’s not the default, script authors may run their scripts with PowerShell v2, allowing attackers to fly under the blue team’s radar because v2 doesn’t support the same security controls as newer versions.
- Is PowerShell logging enabled? Newer versions of PowerShell come with rich logging capabilities that provide insights into which commands are executed.
Lateral Movement
After gaining initial access to an endpoint, e.g., through a phishing attack, threat actors often impersonate legitimate users and move to other systems on the network to gather information, obtain credentials, and escalate privileges. The best defense against such lateral movement is security hardening. uberAgent ESA verifies that such measures are in place with tests such as the following (excerpt):
- Is LAPS implemented? Microsoft’s local administrator password solution (LAPS) ensures that privilege escalation on one endpoint doesn’t give attackers administrative access to all endpoints.
- Is PowerShell remoting disabled? PowerShell remoting allows the remote execution of PowerShell commands. It should be avoided.
Passwordless Login
Modern authentication methods, such as Windows Hello, are more secure and easier for the end user. They’re easier because a fingerprint or face scan is usually sufficient. More secure because biometric login is configured per device, not domain-wide. uberAgent helps organizations set up and maintain safe and compliant biometric authentication with tests such as the following (excerpt):
- Is Windows Hello enabled? Wich devices and users have Windows Hello enabled across the fleet?
- Authentication methods. This test reports available and enabled authentication methods such as camera, fingerprint, or PIN.
Modularity and Openness
uberAgent SCI is both modular and open. This means two things:
No Secret Sauce
All SCI tests are available as source code in our uberAgent Configuration GitHub repository. For example, the PowerShell tests mentioned above can be found here.
As open-source components, uberAgent’s SCI tests can be inspected, audited, improved upon, and contributed to. There is no secret sauce. Instead, you get solid detection engineering that doesn’t try to hide what it can and cannot do.
Customized Compliance Testing
uberAgent’s SCI tests are not a black box. Individual tests can be disabled if not deemed relevant. But more importantly, customers and partners can add tests of their own. This enables robust use cases like the following:
- Verify compliance with an organization’s security policy.
- Check the configuration of line-of-business applications.
Secure and Flexible Operations
Principle of Least Privilege
uberAgent Security & Compliance Inventory has been built with the security and operations requirements of enterprise IT in mind. SCI tests are executed in a sandboxed environment configured for maximum security. The necessary permissions are configured per test so that test scripts only run with minimal required rights and privileges.
Flexible Deployment & Automatic Updates
uberAgent Central Config File Management (CCFM), another new 7.1 feature we announced recently, is the perfect feature companion for Security & Compliance Inventory. CCFM makes it possible to centrally host uberAgent configurations even for huge numbers of endpoints without resorting to Group Policy. With CCFM, endpoints can be assigned the most appropriate configuration depending on department, location, or other properties.
Another cool feature of CCFM is that configuration updates are automatic. Once an updated configuration is published to the central file share, endpoints download and apply it independently. Built-in reporting capabilities put IT in control by showing which configuration is used where.
About uberAgent
The uberAgent product family offers innovative digital employee experience monitoring and endpoint security analytics for Windows and macOS.
uberAgent UXM highlights include detailed information about boot and logon duration, application unresponsiveness detection, network reliability drill-downs, process startup duration, application usage metering, browser performance, web app metrics, and Citrix insights. All these varied aspects of system performance and reliability are smartly brought together in the Experience Score dashboard.
uberAgent ESA excels with a sophisticated Threat Detection Engine, endpoint security & compliance rating, the uAQL query language, detection of risky activity, DNS query monitoring, hash calculation, registry monitoring, and Authenticode signature verification. uberAgent ESA comes with Sysmon and Sigma rule converters, a graphical rule editor, and uses a simple yet powerful query language instead of XML.
About vast limits
vast limits GmbH is the company behind uberAgent, the innovative digital employee experience monitoring and endpoint security analytics product. vast limits’ customer list includes organizations from industries like finance, healthcare, professional services, and education, ranging from medium-sized businesses to global enterprises. vast limits’ network of qualified solution partners ensures best-in-class service and support anywhere in the world.


