uberAgent 7.0 Preview: MITRE ATT&CK Technique ID Integration
While we’re finalizing version 7.0 of our user experience monitoring & endpoint security analytics products uberAgent UXM and uberAgent ESA, let’s take a look at a cool new feature: MITRE ATT&CK technique ID integration.
What Is MITRE ATT&CK?
The MITRE ATT&CK® framework is a knowledge base of adversary tactics and techniques based on real-world observations of cybersecurity threats. With the help of ATT&CK, different stakeholders (offense, defense, SOCs, third-party vendors, and so on) can speak the same language to describe attacks on enterprise IT and mobile devices. While there are other similar frameworks available, ATT&CK is the de-facto industry standard.
Tactics, Techniques, Common Knowledge
ATT&CK stands for adversarial tactics, techniques, and common knowledge. Tactics describe an attacker’s goals, like getting inside your network, techniques show how they do it, e.g., by sending phishing messages. Common knowledge refers to the documentation of procedures.
ATT&CK currently lists 14 enterprise tactics and 191 enterprise techniques with 385 sub-techniques. Each technique has its unique ID. T1071, for example, describes how adversaries may communicate using application layer protocols like DNS to avoid detection or network filtering by blending in with existing traffic.
Each technique’s web page starts with a detailed description, followed by lists of procedure examples, mitigations, and detections. All of that information is now available from uberAgent’s ESA dashboards.
How the uberAgent ATT&CK Integration Works
Threat Detection Rule Definition
uberAgent ESA Threat Detection rules now come with technique ID annotations. Take a look at the following rule that links Cobalt Strike DNS beacon detection with the ATT&CK technique T1071.004:
[ActivityMonitoringRule]
# Detects suspicious DNS queries known from Cobalt Strike beacons
RuleName = Cobalt Strike DNS Beaconing
EventType = Dns.Query
Tag = cobalt-strike-dns-beaconing
RiskScore = 100
Annotation = {"mitre_attack": ["T1071", "T1071.004"]}
Query = (Dns.QueryRequest like r"aaa.stage.%" or Dns.QueryRequest like r"post.1%")
GenericProperty1 = Dns.QueryRequest
GenericProperty2 = Dns.QueryResponseuberAgent ESA Splunk Dashboard Visualization
Whenever a detection rule such as the one shown above matches activity on a monitored endpoint, uberAgent generates an event in your SIEM (typically Splunk).
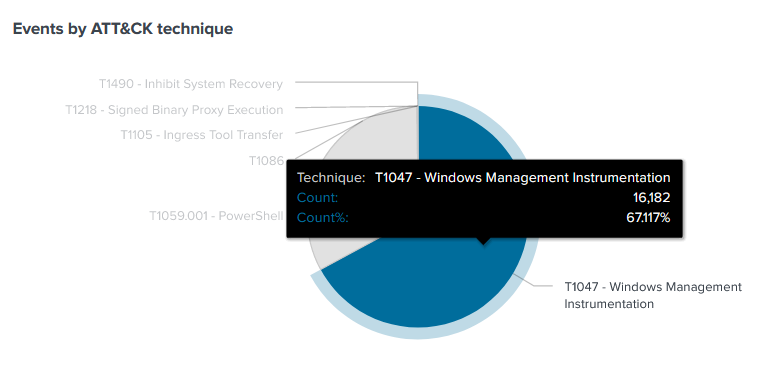
The uberAgent ESA Splunk app visualizes such Threat Detection events and makes them easily accessible. Events can be grouped by various dimensions, e.g., by originating application, or – of course – by ATT&CK technique. In addition to the detailed information uberAgent collects on each event, the dashboard displays a description of the ATT&CK technique associated with the event:
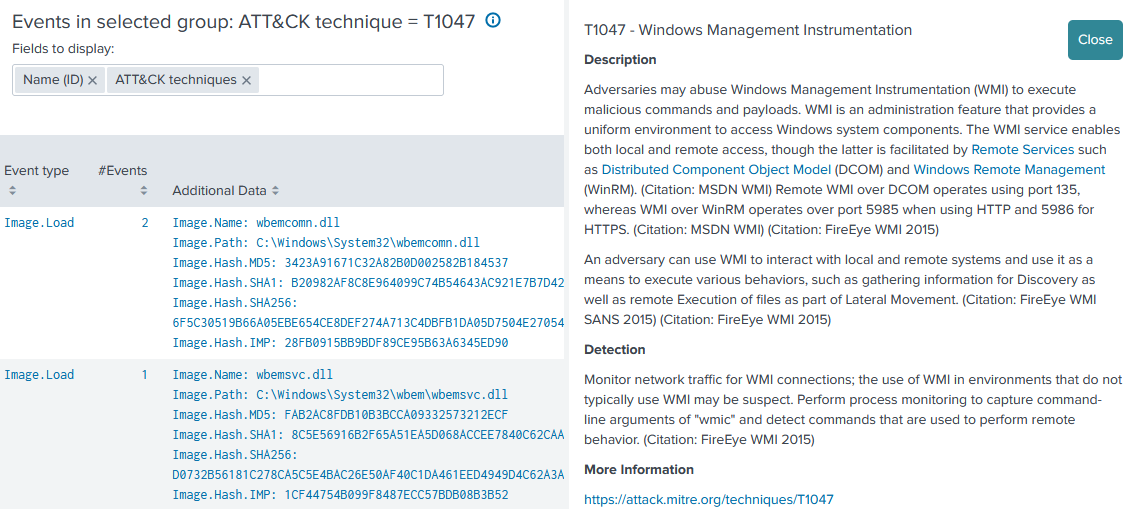
Splunk Enterprise Security Integration
Once you have installed the uberAgent ESA ES companion app, the Splunk Enterprise Security dashboard Risk Analysis is populated automatically with uberAgent data:
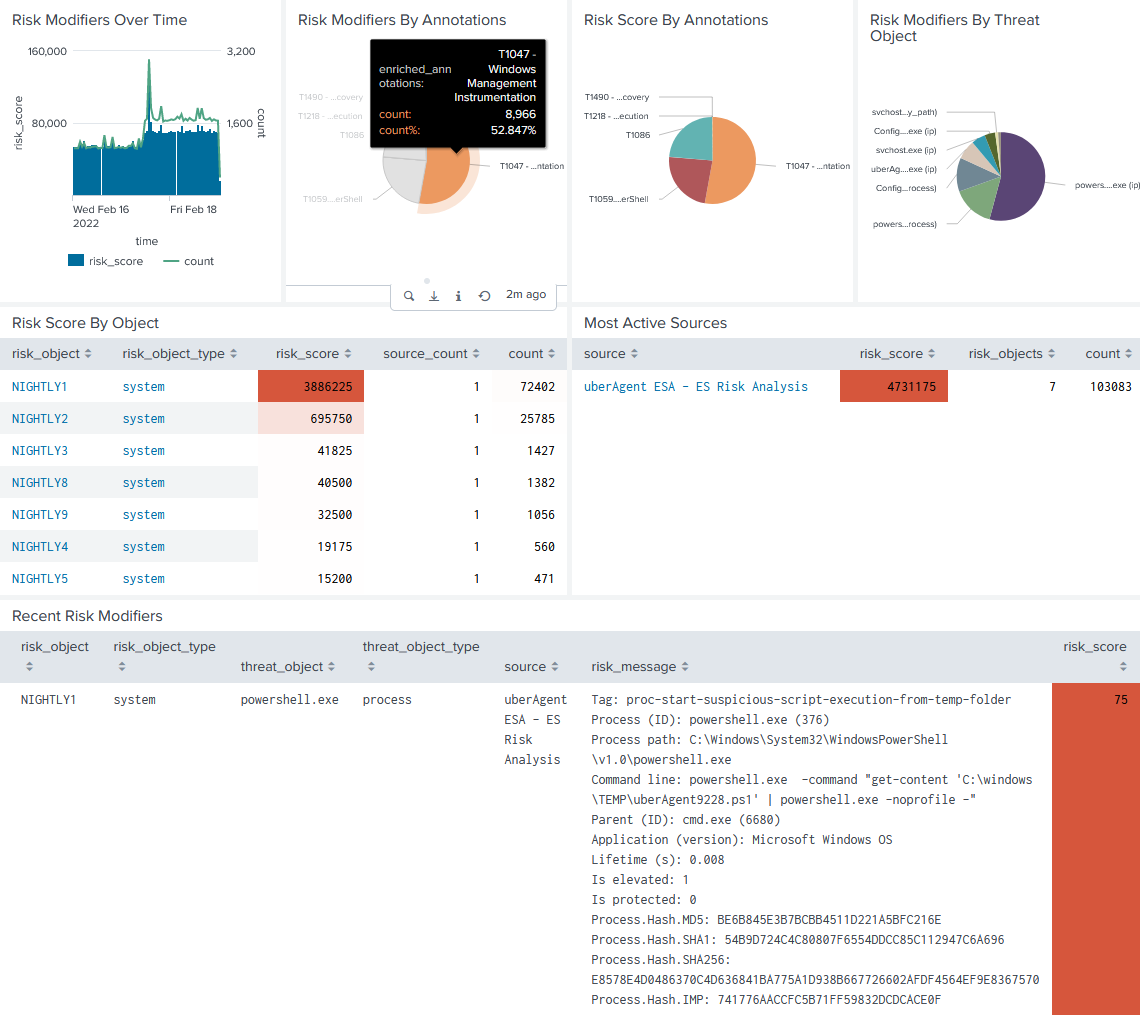
About uberAgent
The uberAgent product family offers innovative digital employee experience monitoring and endpoint security analytics for Windows and macOS.
uberAgent UXM highlights include detailed information about boot and logon duration, application unresponsiveness detection, network reliability drill-downs, process startup duration, application usage metering, browser performance, web app metrics, and Citrix insights. All these varied aspects of system performance and reliability are smartly brought together in the Experience Score dashboard.
uberAgent ESA excels with a sophisticated Threat Detection Engine, endpoint security & compliance rating, the uAQL query language, detection of risky activity, DNS query monitoring, hash calculation, registry monitoring, and Authenticode signature verification. uberAgent ESA comes with Sysmon and Sigma rule converters, a graphical rule editor, and uses a simple yet powerful query language instead of XML.
About vast limits
vast limits GmbH is the company behind uberAgent, the innovative digital employee experience monitoring and endpoint security analytics product. vast limits’ customer list includes organizations from industries like finance, healthcare, professional services, and education, ranging from medium-sized businesses to global enterprises. vast limits’ network of qualified solution partners ensures best-in-class service and support anywhere in the world.


