Monitoring Windows 10 Update Status
Not too long ago it was next to impossible to determine a machine’s exact patch state. That changed with Microsoft’s move to the rollup model. Making patches exclusively available as cumulative monthly bundles enforces a linear update sequence, the current state of which can be represented by a single number, the UBR (update build revision).
What It Was Like Before the Monthly Rollups
For decades, Microsoft had been releasing patches individually. That offered choice, and – seemingly – stability. When a customer noticed a problem with a specific component, they could install patches for that component only, leaving the rest of the system unchanged – at least in theory.
In practice, there are many interdependencies between services, DLLs and the like. Making a change to one often requires making changes to others, too. Imagine one patch requiring a specific change to a common component like Explorer. Bundling the patch with the updated version of Explorer seems like the obvious solution. Now imagine a second patch requiring a different change to Explorer, so it is also bundled with an updated version, but the Explorer update in patch two is different from the Explorer update in patch one. What happens when customer A installs patch one before patch two, while customer B chooses the reverse order?
These kinds of dependencies are very difficult to resolve. Meaningful testing is next to impossible. In other words: it became unmanageable, things had to change.
When Did Microsoft Switch to the Rollup Model?
The switch from individual updates to cumulative rollups was introduced with the first release of Windows 10 in 2015. Windows 7, 8.1 and their server equivalents followed about 1.5 years later.
The Problem With Cumulative Rollups: Size
Cumulative rollups contain all the necessary bits to update any older version of the same OS. Consequently, cumulative updates grow in size over time. The September update will always be bigger than the August update, whereas the October update will, in turn, be bigger than the September update.
Minimizing the Download
Express Update Delivery
Windows 10 uses a sophisticated mechanism called Express to minimize the download volume. In a nutshell it works as follows:
- Windows Update first downloads metadata about an update
- Windows Update passes the metadata to Windows Installer
- Windows Installer scans the system to determines which parts of the update’s files are already present
- Windows Installer requests Windows Update to download the changed byte ranges from the update’s files
- Windows Update downloads the ranges and passes them to Windows Installer so it can patch the OS
Express update delivery for quality updates (i.e. patches) is available for Windows 10 clients connected to:
- System Center Configuration Manager 1702
- WSUS
- Windows Update
- Windows Update for Business
Starting with Windows 10 1709, Express is also being used for feature updates (i.e. new OS versions) for clients connected to:
- Windows Update
- Windows Update for Business
Delta Updates
Delta updates are an interim mechanism only available for Windows 10 versions 1607, 1703 and 1709.
Delta updates are not cumulative; they only contain one month’s patches and can only be applied to machines that have the previous month’s update installed.
Update Linearity and UBR
Individual KB downloads are a thing of the past. This is a big step towards reducing fragmentation caused by systems containing a mix of individual updates.
With a linear update sequence, a machine is always at a well-defined point of a number line. The machine’s current position on the line reflects its update status. The corresponding number is called Update Build Revision (UBR). If you know a machine’s OS build and UBR numbers, you can easily look up its patch state on Microsoft’s Windows 10 release information site.
Monitoring the Windows 10 Patch State
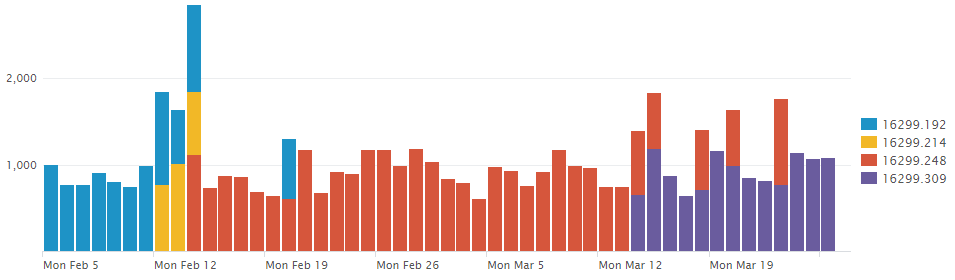
uberAgent performs a daily inventory that includes installed updates as well as the operating system’s build & UBR numbers. While the list of updates can be useful for troubleshooting individual machines, the OS build allows for a great overview of the update health of the estate. The screenshot above, taken from the Update Inventory dashboard, shows the OS build distribution over time. It is easy to see how quality updates are being rolled out, replacing the previous version and incrementing the build number.
About uberAgent
The uberAgent product family offers innovative digital employee experience monitoring and endpoint security analytics for Windows and macOS.
uberAgent UXM highlights include detailed information about boot and logon duration, application unresponsiveness detection, network reliability drill-downs, process startup duration, application usage metering, browser performance, web app metrics, and Citrix insights. All these varied aspects of system performance and reliability are smartly brought together in the Experience Score dashboard.
uberAgent ESA excels with a sophisticated Threat Detection Engine, endpoint security & compliance rating, the uAQL query language, detection of risky activity, DNS query monitoring, hash calculation, registry monitoring, and Authenticode signature verification. uberAgent ESA comes with Sysmon and Sigma rule converters, a graphical rule editor, and uses a simple yet powerful query language instead of XML.
About vast limits
vast limits GmbH is the company behind uberAgent, the innovative digital employee experience monitoring and endpoint security analytics product. vast limits’ customer list includes organizations from industries like finance, healthcare, professional services, and education, ranging from medium-sized businesses to global enterprises. vast limits’ network of qualified solution partners ensures best-in-class service and support anywhere in the world.


