Detecting CVE-2022-30190 (Office RCE) With uberAgent ESA & Splunk
This article explains how to detect the “Follina” remote code execution vulnerability that is exploitable on all current versions of Office 365.
CVE-2022-30190 (Follina) in a Nutshell
This vulnerability is surprisingly easy to exploit. All you need is a malicious DOCX or RTF file and a web server hosting a static HTML page. Both files can be generated easily (for details see the section “Further Reading” below).
In its simplest form, CVE-2022-30190 can be exploited as follows:
- The attacker sends a malicious RTF document to the victim.
- The victim saves the RTF document to disk and navigates to the document’s location in Explorer.
- If Explorer has the preview pane enabled, it starts Word to generate the preview.
- Word opens the RTF, finds the URL to what it thinks is a remote template, but really is an HTML payload, downloads it and processes its content.
- The HTML contains a script tag with a
ms-msdt:URL. The URL includes the target binary to be executed. - The URL is passed to
msdt.exewhich is used as a LOLBIN to execute the target binary.
Detecting CVE-2022-30190 with uberAgent ESA
CVE-2022-30190 can be detected by hunting for cases where WINWORD.EXE starts msdt.exe as a child process. The good news is that uberAgent ESA comes with an Threat Detection rule that logs all MS Office child processes because, with very few exceptions, Office applications should not start any child processes at all.
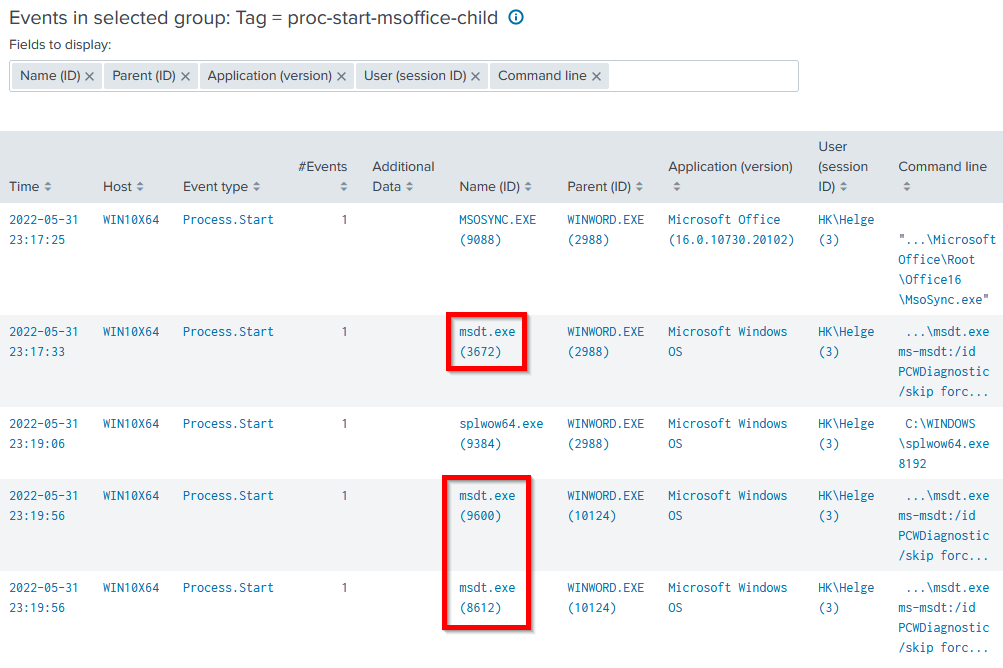
To hunt for CVE-2022-30190, navigate to uberAgent ESA’s Threat Detection Events dashboard and click the tag proc-start-msoffice-child. You should get a table like the one in the screenshot below. It shows two different ways to exploit the vulnerability:
- DOCX: at 23:17:33, a malicious DOCX was double-clicked.
- RTF: at 23:19:56, the same document, but saved as RTF, was rendered in Explorer’s preview pane.
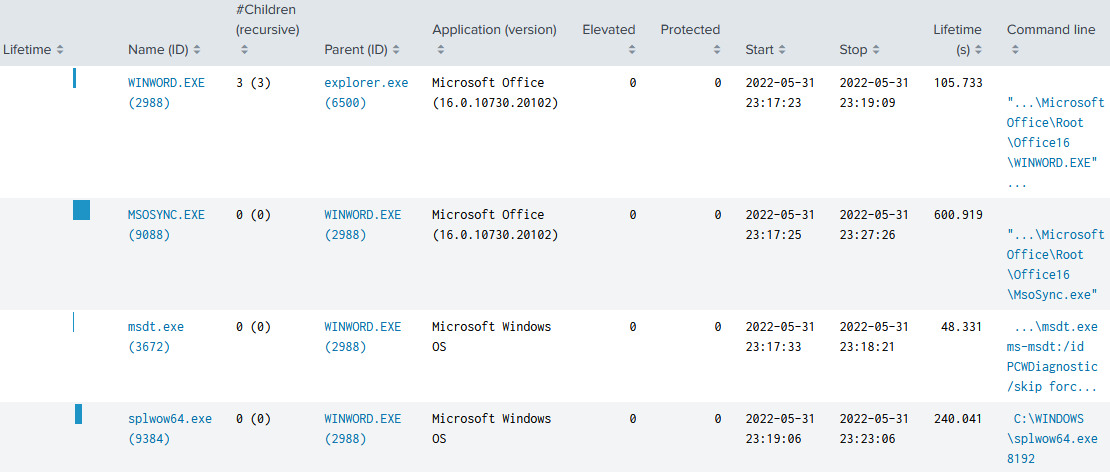
Process Tree: CVE-2022-30190 via DOCX
uberAgent ESA’s Process Tree dashboard shows interesting differences between the two cases. When the vulnerability is exploited by double-clicking a malicious DOCX file, you can see that explorer.exe (PID 6500) starts WINWORD.EXE (PID 2988), which in turn starts msdt.exe (PID 3672):
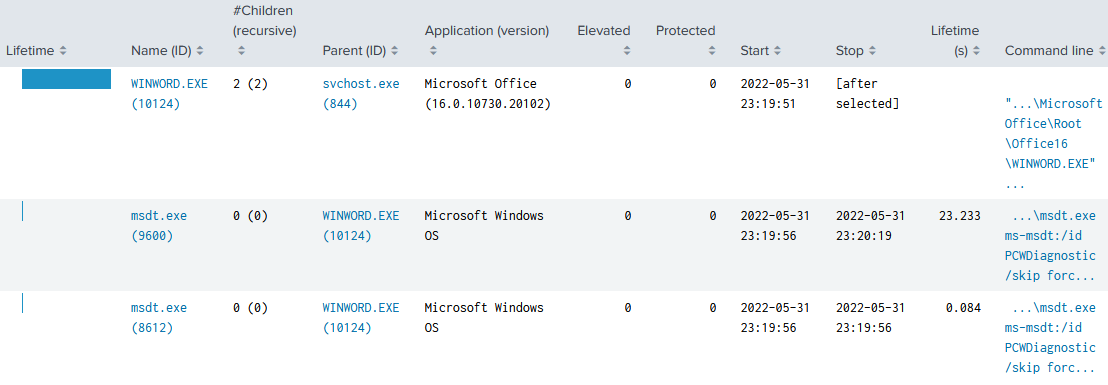
Process Tree: CVE-2022-30190 via RTF in Explorer’s Preview Pane
When the vulnerability is exploited by navigating to a malicious RTF file in Explorer, WINWORD.EXE is not launched by explorer.exe, but by svchost.exe (PID 844). Another difference is that WINWORD.EXE, in turn, launches not one but two instances of msdt.exe:
Targeted Threat Detection Rule for CVE-2022-30190
Of course, you don’t have to rely on uberAgent ESA’s generic rules to detect CVE-2022-30190. Creating and testing custom rules is quick and intuitive with uAQL Studio, uberAgent’s online rule creation tool.
The following Threat Detection rule detects cases where msdt.exe is started as a child process of either Word, Excel, or PowerPoint:
[ActivityMonitoringRule]
# Detect Microsoft Support Diagnostic Tool Vulnerability (CVE-2022-30190)
RuleName = Detect Microsoft Support Diagnostic Tool Vulnerability
EventType = Process.Start
Tag = proc-start-msdt-vulnerability
RiskScore = 75
Query = ((Process.Path like r"%msdt.exe") and (Parent.Path like r"%winword.exe" or Parent.Path like r"%excel.exe" or Parent.Path like r"%powerpnt.exe"))
GenericProperty1 = Parent.Path
Update/Fix
CVE-2022-30190 is fixed in the June 2022 cumulative Windows Update (source).
Further Reading
- Follina — a Microsoft Office code execution vulnerability by Kevin Beaumont
- Rapid Response: Microsoft Office RCE – “Follina” MSDT Attack by John Hammond (Huntress)
- Python script to test the vulnerability by Cas van Cooten. The script generates a malicious DOCX and starts a local web server with the HTML payload referenced by the Word document.
- Instructions to manually create the malicious Word document and the HTML payload by Julien Mousqueton.
About uberAgent
The uberAgent product family offers innovative digital employee experience monitoring and endpoint security analytics for Windows and macOS.
uberAgent UXM highlights include detailed information about boot and logon duration, application unresponsiveness detection, network reliability drill-downs, process startup duration, application usage metering, browser performance, web app metrics, and Citrix insights. All these varied aspects of system performance and reliability are smartly brought together in the Experience Score dashboard.
uberAgent ESA excels with a sophisticated Threat Detection Engine, endpoint security & compliance rating, the uAQL query language, detection of risky activity, DNS query monitoring, hash calculation, registry monitoring, and Authenticode signature verification. uberAgent ESA comes with Sysmon and Sigma rule converters, a graphical rule editor, and uses a simple yet powerful query language instead of XML.
About vast limits
vast limits GmbH is the company behind uberAgent, the innovative digital employee experience monitoring and endpoint security analytics product. vast limits’ customer list includes organizations from industries like finance, healthcare, professional services, and education, ranging from medium-sized businesses to global enterprises. vast limits’ network of qualified solution partners ensures best-in-class service and support anywhere in the world.


